afae.sys
ไฟล์ที่ใช้ทดสอบ Setup.exe
File size: 148496 bytes
MD5 : 293d93e2d365176355475d98c023a27f
SHA1 : 593e7928e01ed61f50683f048fde0d452bc13881
...
| Antivirus | Version | Last Update | Result |
|---|---|---|---|
| a-squared | 5.0.0.31 | 2010.07.05 | Trojan.Win32.SuspectCRC!IK |
| AhnLab-V3 | 2010.07.03.00 | 2010.07.03 | Win-Trojan/Rootkit.148496 |
| AntiVir | 8.2.4.2 | 2010.07.05 | TR/Agent.eeyu |
| Antiy-AVL | 2.0.3.7 | 2010.07.02 | Trojan/Win32.Agent.gen |
| Authentium | 5.2.0.5 | 2010.07.05 | - |
| Avast | 4.8.1351.0 | 2010.07.05 | Win32:Rootkit-gen |
| Avast5 | 5.0.332.0 | 2010.07.05 | Win32:Rootkit-gen |
| AVG | 9.0.0.836 | 2010.07.05 | SHeur3.ABNI |
| BitDefender | 7.2 | 2010.07.05 | Trojan.Generic.4129422 |
| CAT-QuickHeal | 11.00 | 2010.06.30 | Trojan.Agent.eeyu |
| ClamAV | 0.96.0.3-git | 2010.07.05 | - |
| Comodo | 5329 | 2010.07.05 | TrojWare.Win32.Trojan.Agent.Gen |
| DrWeb | 5.0.2.03300 | 2010.07.05 | - |
| eSafe | 7.0.17.0 | 2010.07.05 | - |
| eTrust-Vet | 36.1.7687 | 2010.07.05 | - |
| F-Prot | 4.6.1.107 | 2010.07.05 | - |
| F-Secure | 9.0.15370.0 | 2010.07.05 | Trojan.Generic.4129422 |
| Fortinet | 4.1.133.0 | 2010.07.04 | W32/Mdrop.CPK!tr |
| GData | 21 | 2010.07.05 | Trojan.Generic.4129422 |
| Ikarus | T3.1.1.84.0 | 2010.07.05 | Trojan.Win32.SuspectCRC |
| Jiangmin | 13.0.900 | 2010.07.03 | Trojan/Agent.dynz |
| Kaspersky | 7.0.0.125 | 2010.07.05 | Trojan.Win32.Agent.eeyu |
| McAfee | 5.400.0.1158 | 2010.07.05 | Generic Dropper!dev |
| McAfee-GW-Edition | 2010.1 | 2010.07.05 | Heuristic.BehavesLike.Win32.Worm.D |
| Microsoft | 1.5902 | 2010.07.03 | TrojanDropper:Win32/Udslee.gen!A |
| NOD32 | 5253 | 2010.07.05 | Win32/Rootkit.Agent.NRP |
| Norman | 6.05.10 | 2010.07.05 | Agent.UVJY |
| nProtect | 2010-07-05.01 | 2010.07.05 | Trojan.Generic.4129422 |
| Panda | 10.0.2.7 | 2010.07.05 | Trj/Downloader.MDW |
| PCTools | 7.0.3.5 | 2010.07.05 | Trojan.ADH |
| Prevx | 3.0 | 2010.07.05 | - |
| Rising | 22.55.00.04 | 2010.07.05 | Trojan.Win32.Generic.521B2417 |
| Sophos | 4.54.0 | 2010.07.05 | - |
| Sunbelt | 6546 | 2010.07.05 | Trojan.Win32.Generic!BT |
| Symantec | 20101.1.0.89 | 2010.07.05 | Trojan.ADH |
| TheHacker | 6.5.2.1.308 | 2010.07.05 | - |
| TrendMicro | 9.120.0.1004 | 2010.07.05 | - |
| TrendMicro-HouseCall | 9.120.0.1004 | 2010.07.05 | - |
| VBA32 | 3.12.12.5 | 2010.07.05 | Trojan.Win32.Agent.eeyu |
| ViRobot | 2010.6.29.3912 | 2010.07.05 | - |
| VirusBuster | 5.0.27.0 | 2010.07.05 | Trojan.Agent.WKTZ |
...
Keys added
HKLM\SYSTEM\ControlSet\Services\afae
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Control
HKLM\SYSTEM\ControlSet001\Services\afae
HKLM\SYSTEM\ControlSet001\Services\afae\Security
HKLM\SYSTEM\ControlSet001\Services\afae\Enum
HKLM\SYSTEM\ControlSet002\Services\afae
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Control
HKLM\SYSTEM\CurrentControlSet\Services\afae
HKLM\SYSTEM\CurrentControlSet\Services\afae\Security
HKLM\SYSTEM\CurrentControlSet\Services\afae\Enum
Values added
HKLM\SYSTEM\ControlSet\Services\afae\access: 6B 78 47 4E 71 63 5A 31 4A 33 69 42 2B 53 59 4A 50 61 4B 58 50 79 6D 63 69 4B 66 62 4E 58 39 77 2F 6D 37 73 4A 70 49 52 54 76 43 4F
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Control\*NewlyCreated*: 0x00000000
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Control\ActiveService: "afae"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Service: "afae"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Legacy: 0x00000001
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\ConfigFlags: 0x00000000
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\Class: "LegacyDriver"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\ClassGUID: "{8ECC055D-047F-11D1-A537-0000F8753ED1}"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\0000\DeviceDesc: "afae"
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE\NextInstance: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\afae\Enum\0: "Root\LEGACY_AFAE\0000"
HKLM\SYSTEM\ControlSet001\Services\afae\Enum\Count: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\afae\Enum\NextInstance: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\afae\Security\Security: 01 00 14 80 90 00 00 00 9C 00 00 00 14 00 00 00 30 00 00 00 02 00 1C 00 01 00 00 00 02 80 14 00 FF 01 0F 00 01
HKLM\SYSTEM\ControlSet001\Services\afae\Type: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\afae\Start: 0x00000001
HKLM\SYSTEM\ControlSet001\Services\afae\ErrorControl: 0x00000000
HKLM\SYSTEM\ControlSet001\Services\afae\Tag: 0x0000001C
HKLM\SYSTEM\ControlSet001\Services\afae\ImagePath: "\??\C:\WINDOWS\system32\afae.sys"
HKLM\SYSTEM\ControlSet001\Services\afae\DisplayName: "afae"
HKLM\SYSTEM\ControlSet001\Services\afae\Group: "PNP_TDI"
HKLM\SYSTEM\ControlSet001\Services\afae\DependOnService: 'tcpip'
HKLM\SYSTEM\ControlSet001\Services\afae\DependOnGroup: 00
HKLM\SYSTEM\ControlSet001\Services\afae\access: 6B 78 47 4E 71 63 5A 31 4A 33 69 42
HKLM\SYSTEM\ControlSet002\Services\afae\access: 6B 78 47 4E 71 63 5A 31 4A 33 69 42
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Control\*NewlyCreated*: 0x00000000
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Control\ActiveService: "afae"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Service: "afae"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Legacy: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\ConfigFlags: 0x00000000
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\Class: "LegacyDriver"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\ClassGUID: "{8ECC055D-047F-11D1-A537-0000F8753ED1}"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\0000\DeviceDesc: "afae"
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE\NextInstance: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\afae\Enum\0: "Root\LEGACY_AFAE\0000"
HKLM\SYSTEM\CurrentControlSet\Services\afae\Enum\Count: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\afae\Enum\NextInstance: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\afae\Security\Security: 01 00 14 80 90 00 00
HKLM\SYSTEM\CurrentControlSet\Services\afae\Type: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\afae\Start: 0x00000001
HKLM\SYSTEM\CurrentControlSet\Services\afae\ErrorControl: 0x00000000
HKLM\SYSTEM\CurrentControlSet\Services\afae\Tag: 0x0000001C
HKLM\SYSTEM\CurrentControlSet\Services\afae\ImagePath: "\??\C:\WINDOWS\system32\afae.sys"
HKLM\SYSTEM\CurrentControlSet\Services\afae\DisplayName: "afae"
HKLM\SYSTEM\CurrentControlSet\Services\afae\Group: "PNP_TDI"
HKLM\SYSTEM\CurrentControlSet\Services\afae\DependOnService: 'tcpip'
HKLM\SYSTEM\CurrentControlSet\Services\afae\DependOnGroup: 00
HKLM\SYSTEM\CurrentControlSet\Services\afae\access: 6B 78 47 4E 71 63 5A 31 4A 33 69
==================================================
วิธีแก้ไข : afae.sys
==================================================
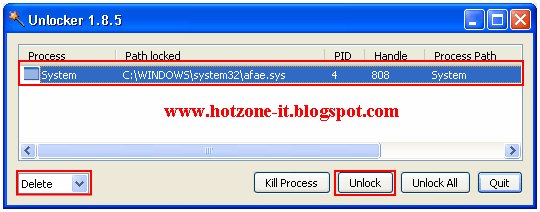
Fix Tool : Unlocker
1. ไปที่ C:\Windows\System32 แล้วหาไฟล์ afae.sys เมื่ื่อพบแล้่ว Click ขวาที่ไฟล์
เลือกที่ Unlocker จะขึ้น หน้าต่าง Unlocker ให้เลือกที่ Delete แล้ว Click ที่บรรทัด system
เลือกที่ Unlock ดังภาพ
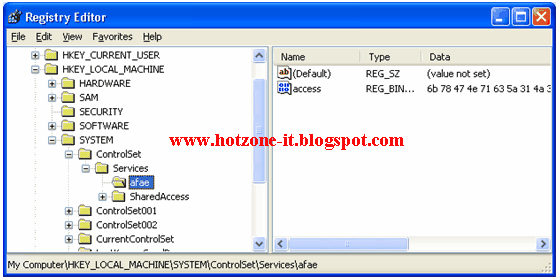
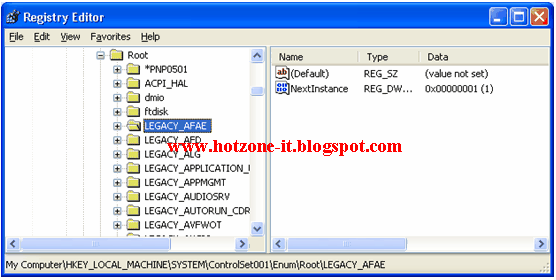
2. ไปที่ Start > Run พิมพ์ regedit.exe แล้ว enter เมื่อขึ้นหน้าต่าง Registry Editor
ให้ลบ Key เหล่านี้ทิ้งไป
HKLM\SYSTEM\ControlSet\Services\afae
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_AFAE
HKLM\SYSTEM\ControlSet001\Services\afae
HKLM\SYSTEM\ControlSet002\Services\afae
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_AFAE
HKLM\SYSTEM\CurrentControlSet\Services\afae
ตัวอย่้างดังภาพ



ไม่มีความคิดเห็น:
แสดงความคิดเห็น