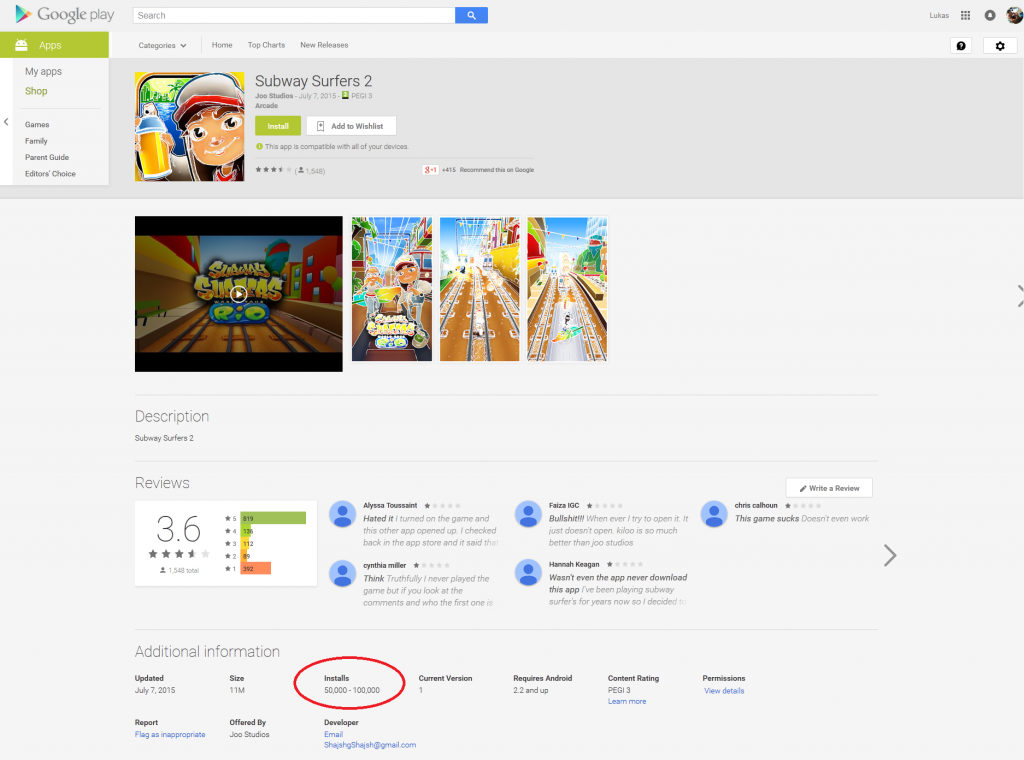
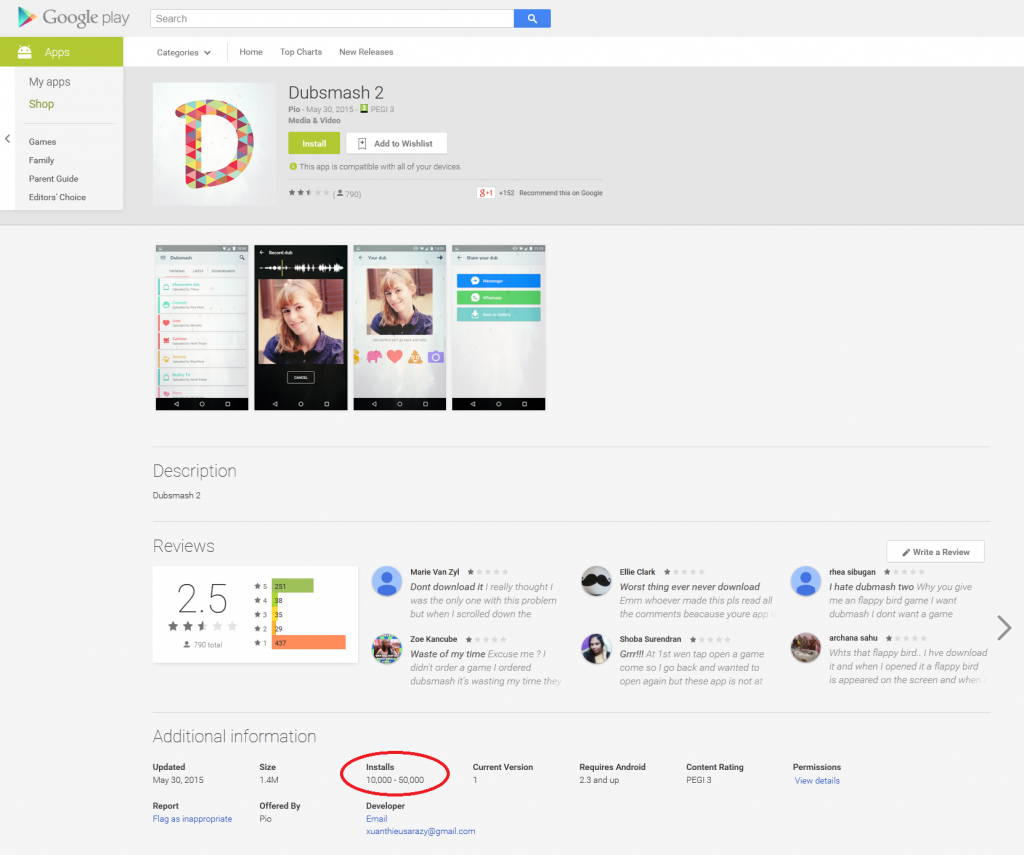
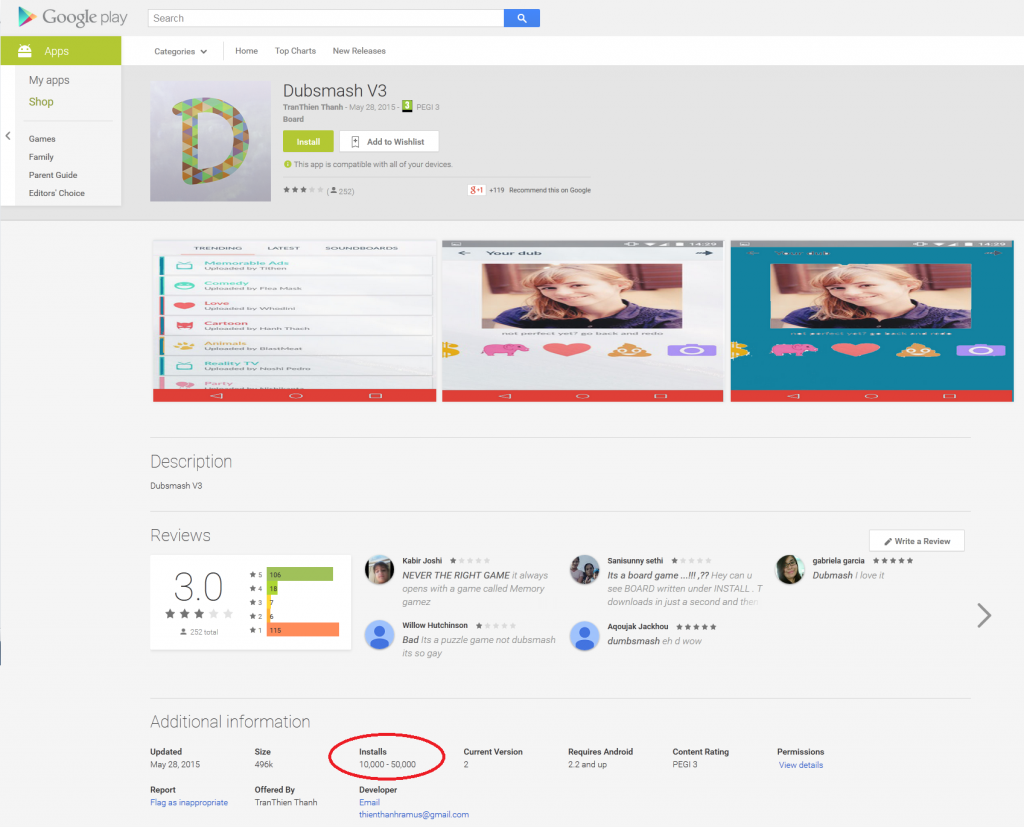
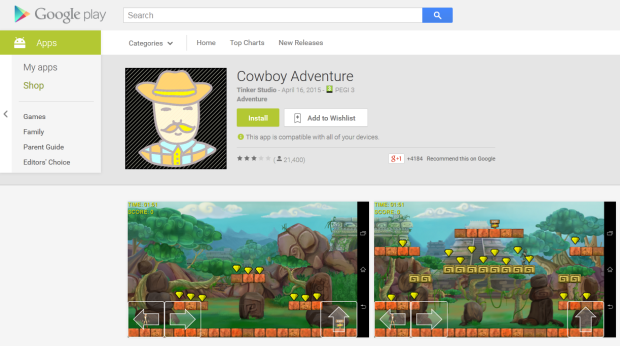
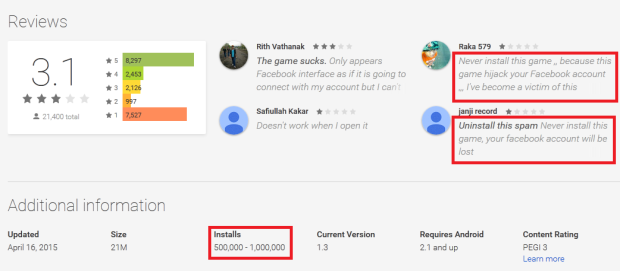
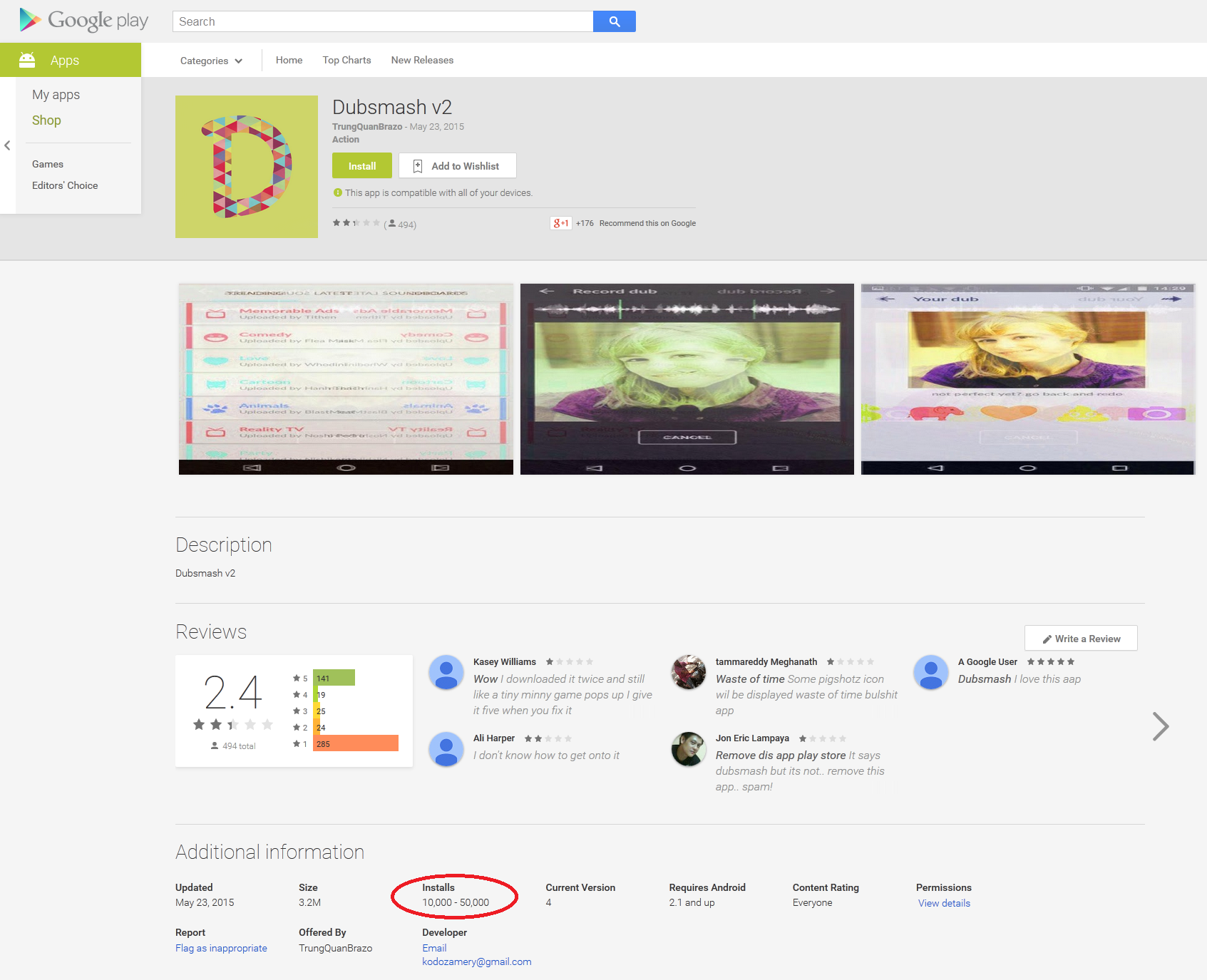
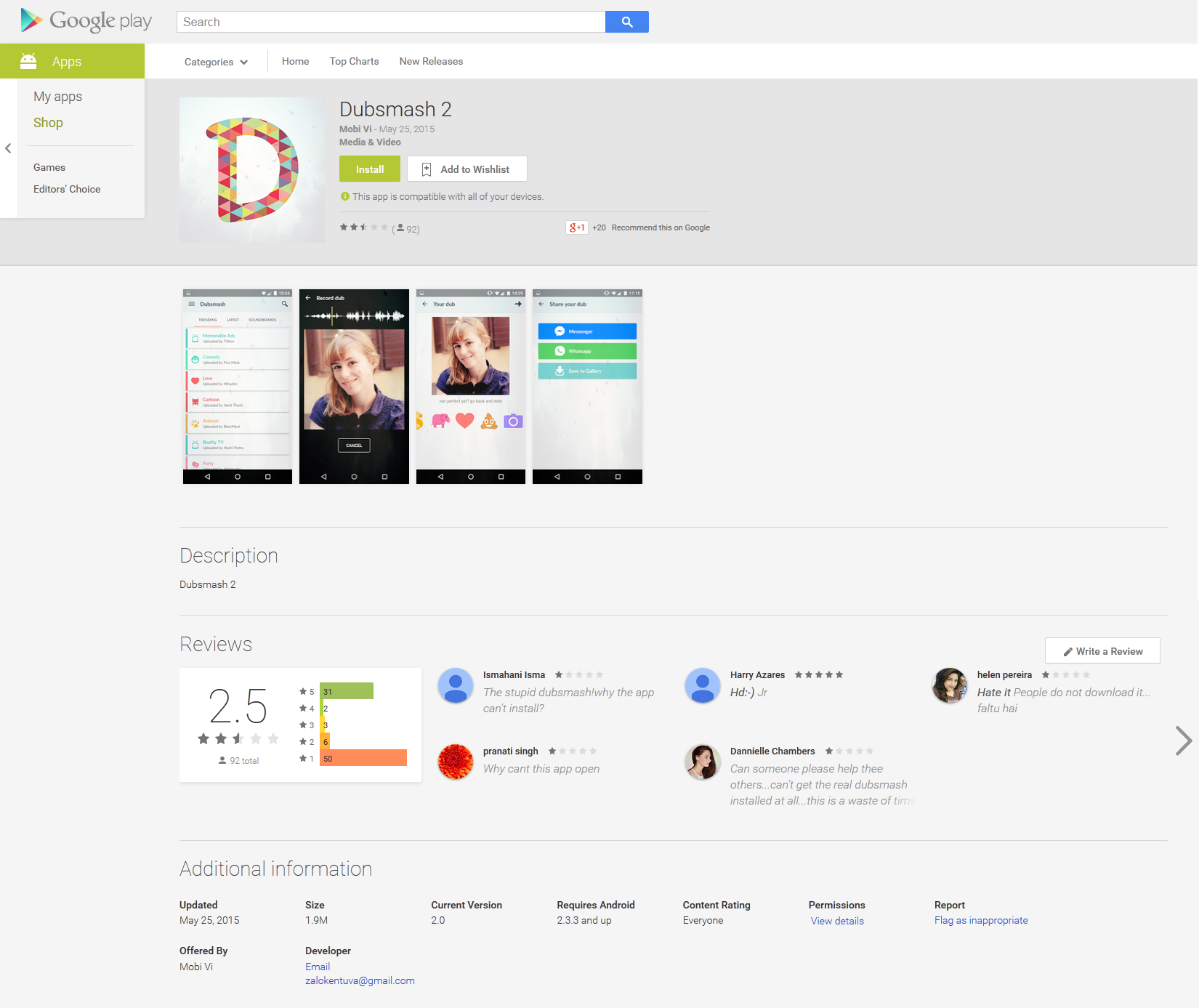
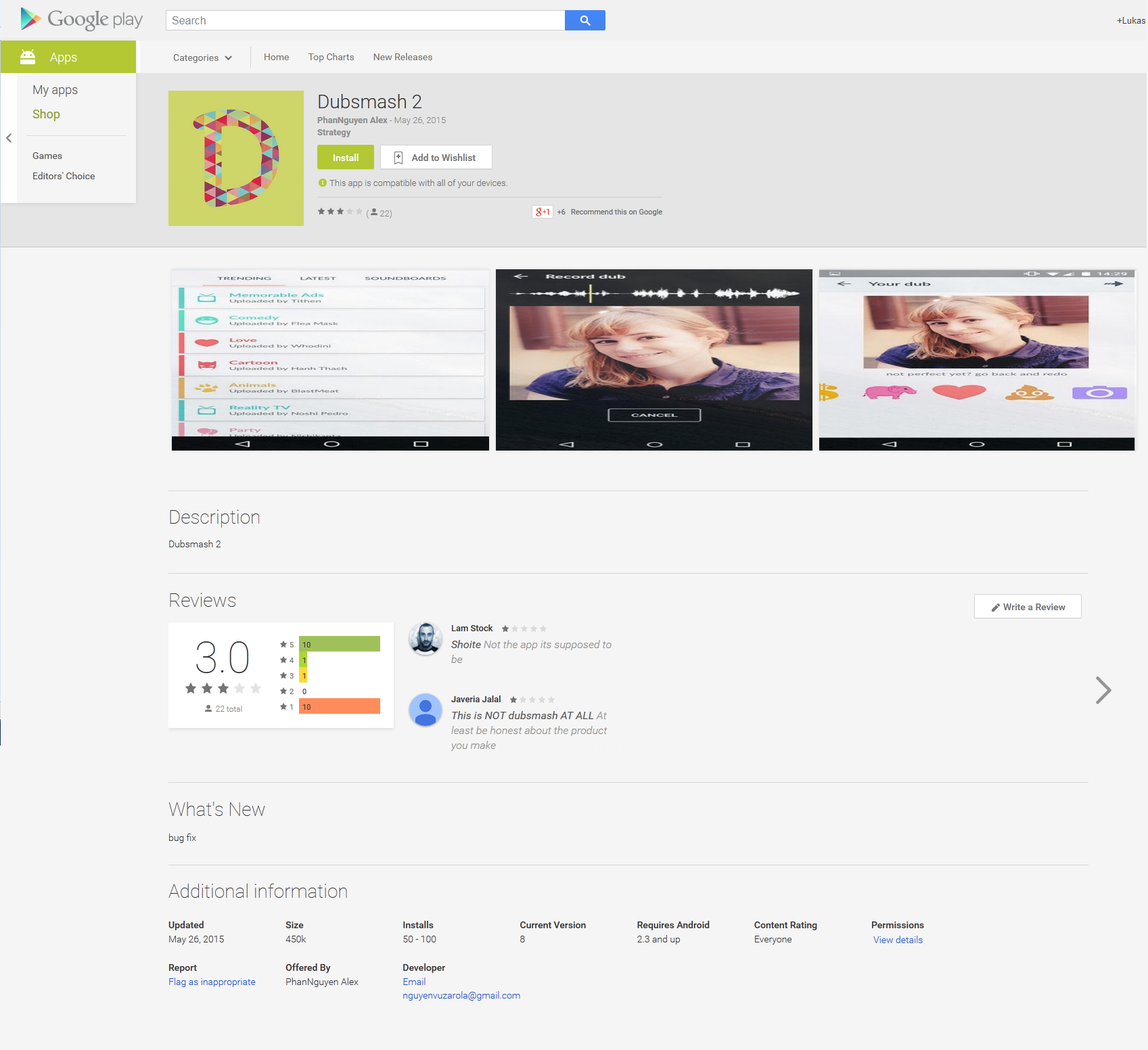
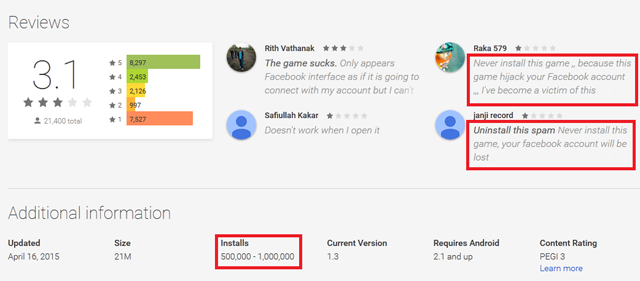
Lately we informed you how a fake Dubsmash application has been uploaded to Google Play Store at least nine times, which have tens of thousands of installs. This porn clicker Trojan, which we detect as Android/Clicker, has once more become available for download from Play Store. After we notified Google and published an article about these fake Dubsmash Trojans, we discovered other fake Dubsmash versions being uploaded again infected with the same porn clicker. We detected yet another 51 Trojan porn clickers accessible for the users to download. Four of them had more than 10,000 installs and one of them had more than 50,000 installs.
This 51 together with 9 fake Dubsmash we reported in the previous article users were able to download 60 different Trojan clicker applications from Google Play. These Trojan clickers were downloaded at least 210,000 times in the last three months. In the weeks after our article was published, these apps were installed more than 106,000 times.
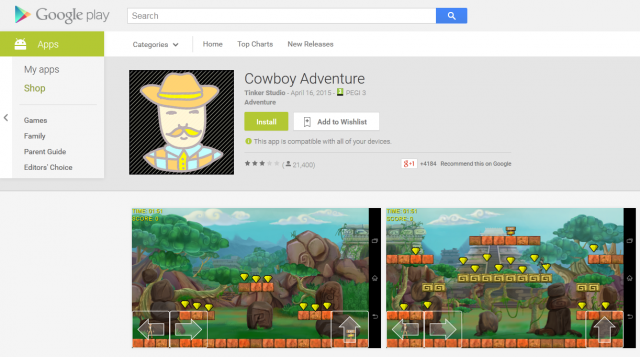
This time not only were fake versions of Dubsmash uploaded by the same developer, we also found Download Manager, Pou 2, Clash of Clans 2, Subway surfers 2, Subway surfers 3, Minecraft 3, Hay Day 2, various game cheats and Video Downloaders being infected with the same Trojan Clicker.
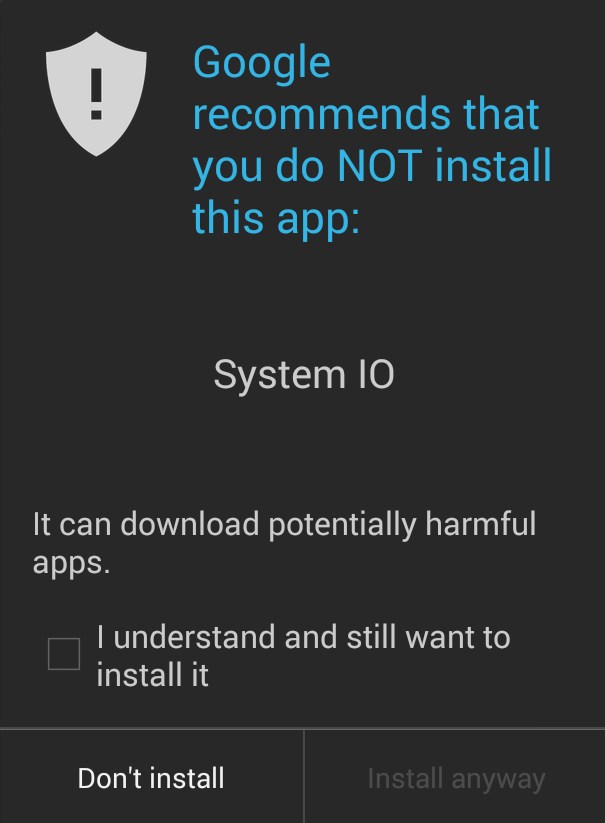
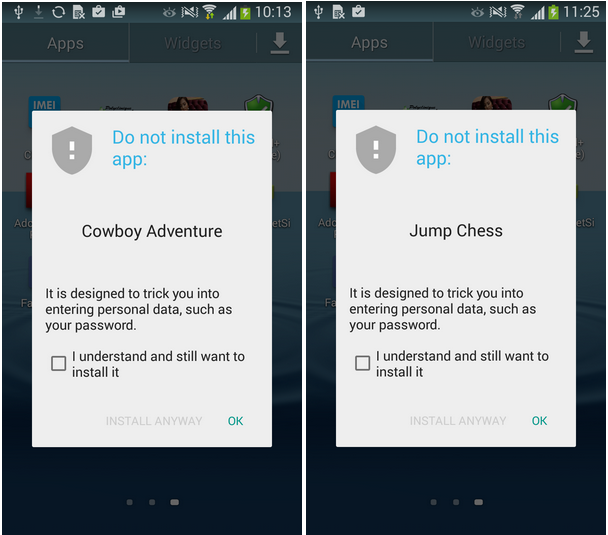
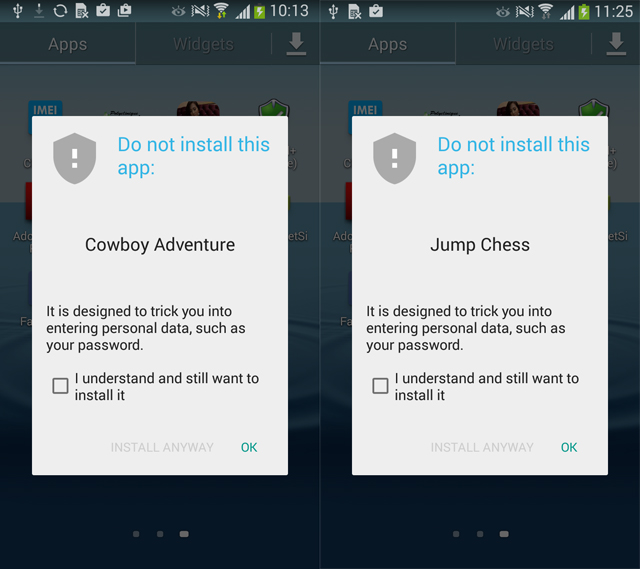
ESET is still seeing occurrences of this infiltration on Google Play and, after more than a month, these fake Trojan Clickers are still managing to evade Google’s Bouncer malware filter and potentially exposing millions of users to risk.
Interestingly, none of the fake applications will add a Dubsmash app icon to the app menu after installation. Instead the malicious apps pretend to be arcade games like Flappy Birds Family, board games or system applications.
Following ESET’s notification, Google has pulled the malware from the Play Store and also reports some of them as potentially harmful applications using its built-in security service.
Conclusion
Even though the malicious applications were available for download for at most a week, tens of thousands of people still installed them. Hopefully, Google is doing its best to fix this issue and find a way to prevent the developers of these porn clickers from publishing them to the Play Store. To reduce the risk from malicious apps that may have slipped through Google’s filtering, we advise Play Store customers to take careful note of reviews by other customers, and to ensure that their security software is kept up to date.More information
App Name
|
Uploaded
|
Installs
|
|---|---|---|
| Dubsmash 2 | 27 May 2015 | 0 - 10 |
| Dubsmash V3 | 28 May 2015 | 10,000 – 50,000 |
| Dubsmash 2 | 30 May 2015 | 10,000 – 50,000 |
| Dubsmash 2 | 2 June 2015 | 0 - 10 |
| Dubsmash 2 | 4 June 2015 | 0 - 10 |
| Dubsmash 3 | 9 June 2015 | 0 - 10 |
| Download Manager | 9 June 2015 | 0 - 10 |
| Dubsmash 2 | 10 June 2015 | 0 - 10 |
| Poo Video Downloader | 13 June 2015 | 0 - 10 |
| Dubsmash 2 | 14 June 2015 | 10 - 50 |
| Dubsmash 2 | 17 June 2015 | 10,000 – 50,000 |
| Dubsmash 3 | 19 June 2015 | 1,000 – 5,000 |
| Dubsmash 2 | 20 June 2015 | 10 - 50 |
| Best : Dubsmash 3! | 1 July 2015 | 0 - 10 |
| Komboatic | 1 July 2015 | 0 - 10 |
| Best : Dubsmash | 4 July 2015 | 10,000 - 50,000 |
| C l a s h o f C l a n s 2 | 4 July 2015 | 100 - 500 |
| Cheats for Clash of Clans | 6 July 2015 | 5,000 - 10,000 |
| Dubs Mash 2 | 6 July 2015 | 1,000 - 5,000 |
| Cheats & Trucos: Gta 5 | 6 July 2015 | 10 – 50 |
| Maps & Guide: GTA 5 | 6 July 2015 | 100 – 500 |
| Subway Surfers 2 | 7 July 2015 | 50,000 – 100,000 |
| Best : Dubsmash | 7 July 2015 | 1,000 – 5,000 |
| Clash of Clans 2 | 8 July 2015 | 0 - 10 |
| Pou 2 | 8 July 2015 | 5,000 - 10,000 |
| Subway Surfers 3 | 8 July 2015 | 1,000 - 5,000 |
| Followers for Instagram | 8 July 2015 | 10 - 50 |
| MayHayda | 8 July 2015 | 500 - 1,000 |
| MayHada | 8 July 2015 | 500 - 1,000 |
| Man Kaptasi | 8 July 2015 | 100 - 500 |
| Smash Hit 2 | 9 July 2015 | 500 – 1,000 |
| Miviki yanki | 10 July 2015 | 1,000 – 5,000 |
| Flipagram 2 | 10 July 2015 | 100 – 500 |
| Koday | 10 July 2015 | 0 - 10 |
| Deer Hunter 2015 | 10 July 2015 | 0 - 10 |
| Minecraft 3 | 13 July 2015 | 0 - 10 |
| Red Ball 6 | 13 July 2015 | 50 - 100 |
| Archery Master 4 | 13 July 2015 | 0 - 10 |
| Exploration Lite 2 | 14 July 2015 | 100 - 500 |
| Traffic Racer 2 | 14 July 2015 | 50 - 100 |
| Hitman Sniper 2 | 14 July 2015 | 50 - 100 |
| Batman 2 | 14 July 2015 | 10 - 50 |
| The Walking Dead 2 | 14 July 2015 | 0 - 10 |
| Moto Loko 2 | 14 July 2015 | 0 - 10 |
| Rally Racer 2 | 14 July 2015 | 0 - 10 |
| Dr Driving 2 | 14 July 2015 | 100 - 500 |
| Survivor Heroes 2 | 15 July 2015 | 0 - 10 |
| Dubsmash 2 | 15 July 2015 | 10 – 50 |
| Hay Day 2 | 15 July 2015 | 0 -10 |
| Subway Surfers 2 | 19 July 2015 | 10 - 50 |
| Dubsmash 2 | 19 July 2015 | 10 - 50 |
Package Name
|
MD5
|
ESET Detection name
|
||
|---|---|---|---|---|
| com.chbded.chs | 73DB1E459DA78A7C831209B687B6C12F | Android/Clicker.M | ||
| com.jet.cleandub | 9334DAD2F7C9422E0D1C740D646C19DB | Android/Clicker.J | ||
| com.jet.dubsh | 48A4BE6A7A6CBAB9C4A674F99E5158AA | Android/Clicker.J | ||
| com.memr.gamess | AC8D9DEEE2B07EF3A7C5BD2FC01560F1 | Android/Clicker.M | ||
| com.androsadfg.downloadmanager | 6CACBDD667504DC564050D5DD5CF683B | Android/Clicker.M | ||
| com.jet.ayak | 28C5A7E4FC2E7CD446E03A88939596FD | Android/Clicker.P | ||
| com.wngrd.mp3remote | 093412BCA7984039F5369DE6308D4C47 | Android/Clicker.M | ||
| com.jet.shdub | 11D32B18A096AE2D0F3D054BA0131492 | Android/Clicker.J | ||
| com.poo.downloader | B85EEF771BE83A33E233A8CA587C9B9D | Android/Clicker.P | ||
| com.poo.db | 88C8F6715D5466DA7C1EB7DBAB7584A8 | Android/Clicker.P | ||
| com.poo.smm | 13AFF08E4733C953BC7DE6A5D7C02FD2 | Android/Clicker.P | ||
| com.huynoibomira.bobo | A845279F215ED6966B45D64E3369A1F2 | Android/Clicker.M | ||
| com.ti.basegam | 656E573C1277EE6607A0403CAA02AE25 | Android/Clicker.M | ||
| com.biz2048.yilinda | 331C93AFACD1433A2ECD7E5E7AEE9ADF | Android/Clicker.M | ||
| com.rikona.sa | 390AE01ED49CBBE14EA91F347E806D8F | Android/Clicker.M | ||
| com.kankalar.cheats | 167ABC463BC9C7A2D1EDC0E383806499 | Android/Clicker.M | ||
| com.kankalar.clash2 | F297E5A18A4025ECB0F34C8BF905B3F1 | Android/Clicker.M | ||
| com.kankalar.elma | 5AF9E1DE3D1D19DACB1AA98288E1CA25 | Android/Clicker.M | ||
| com.sulale.chetastga | 08B320694B898B0F6402FA8B45D301F8 | Android/Clicker.M | ||
| com.sulale.cimmi | 249A0660F18C53D91B58A680D78E9EC4 | Android/Clicker.M | ||
| com.sulale.dubb | D11BB0B91595E6B6DE89FB7BF2C92F83 | Android/Clicker.M | ||
| com.poo.cofc | 4FBC4AB39C704088902A6C114A44F0F3 | Android/Clicker.Q | ||
| com.poo.po | 98961261BC663F4D3E6F073CE6575A48 | Android/Clicker.Q | ||
| com.poo.way | 3E62E455A15D99762198F8C5779F81AF | Android/Clicker.Q | ||
| com.poo.x | DC78620AA75EDBB846776760A88AE17A | Android/Clicker.Q | ||
| com.nguyenngocjumraze.suuu | 21679FE29217DB6925B17CC4BF1FCE9B | Android/Clicker.M | ||
| com.nguyenngocjumraze.takip | 3FD37BB6250F08A58C8932C630F57C4C | Android/Clicker.M | ||
| com.fet.hiye | 47BE311A6CDA5B4981DB282CA1884BC9 | Android/Clicker.M | ||
| com.kendo.yako | B0345E9392F2C79D2403B18FB7FFD419 | Android/Clicker.M | ||
| com.nhantieplosengazi.flip | 44D7A2E9B3D106C4D41311E23350A813 | Android/Clicker.M | ||
| com.nhantieplosengazi.kivi | 189E5E23A99AF963DBFD70FD9552661E | Android/Clicker.M | ||
| com.phutanjocohare.conc | CB6A3918CFFA7BEEF2EAD6E5C60F2A3E | Android/Clicker.M | ||
| com.phutanjocohare.jat | 647987E48CF037E57CEEC6CB282F8124 | Android/Clicker.M | ||
| com.phutanjocohare.may | 9E4B0ADC7B4CF2353859EADBB928C688 | Android/Clicker.M | ||
| com.pupa.yelken | 5B35B0D5E04F9CDCFFF66D376805ADDF | Android/Clicker.M | ||
| com.xuanjonaterilove.sma | 402AEF32A99C71602A51FF8A36F5ABFE | Android/Clicker.M | ||
| com.fryzombisaren.haa | 4462CDA324E272FA63511D77486B82B9 | Android/Clicker.M | ||
| com.fryzombisaren.hte | 12D2DF188BAF7523BB04AC7735E6C818 | Android/Clicker.M | ||
| com.cor2.lu | FAD2ABC5DBD0F081EB3E9509EA7840E9 | Android/Clicker.M | ||
| com.eski.hisar | 8C4AC0AD1435264D3219DB45FEC627F9 | Android/Clicker.M | ||
| com.isken.derun | EC6359CEF3E0933467F62DD31F20AF09 | Android/Clicker.M | ||
| com.kasta.monu | 0D93F4278FC8288CEAA8FE5933BA64C6 | Android/Clicker.M | ||
| com.manisa.turgutlu | FFB92BA3236CC5C9DF9A2EF5EDB3BDE2 | Android/Clicker.M | ||
| com.pamuk.kale | 474EA15E00B1EF9A29F1BF624B78FA4B | Android/Clicker.M | ||
| com.thanhbangzerisa.bat | 1C4C8380C51CECDA01D40A841601A0BD | Android/Clicker.M | ||
| com.thanhbangzerisa.de | FE6B42F3872014C1CB4374611676B754 | Android/Clicker.M | ||
| com.thanhbangzerisa.ex | 97804ADBA13B706A3EA232FD28DC9B4D | Android/Clicker.M | ||
| com.thanhbangzerisa.hi | AF96768436794CE6161A4A62C82F5A0D | Android/Clicker.M | ||
| com.thanhbangzerisa.tita | E3E4984C3143B8461B38B187A31A0BEF | Android/Clicker.M | ||
| com.xuantonglazaderi.du | D59B2C7A28AE19FF2B85DB9C2EEEF29B | Android/Clicker.M | ||
| com.xuantonglazaderi.su2 | 1E5B2B33CF0A4AE45BF29C7C848C5F60 | Android/Clicker.M |
ที่มา : welivesecurity.com