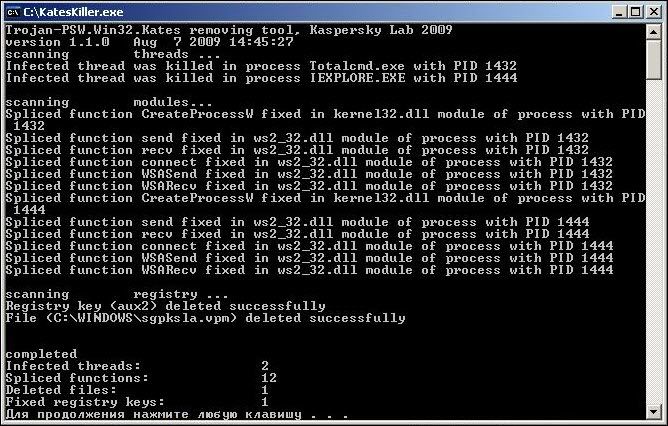
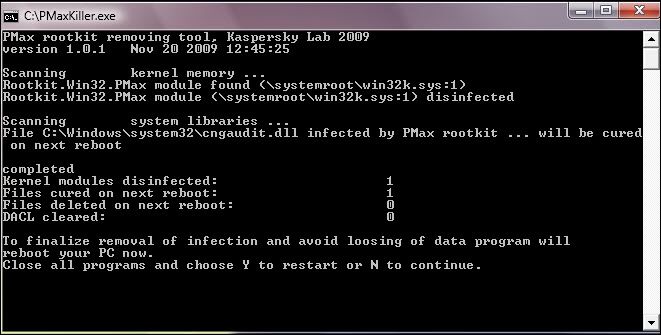
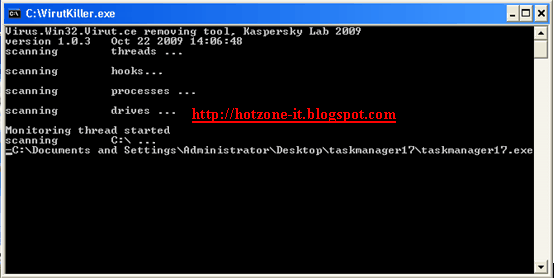
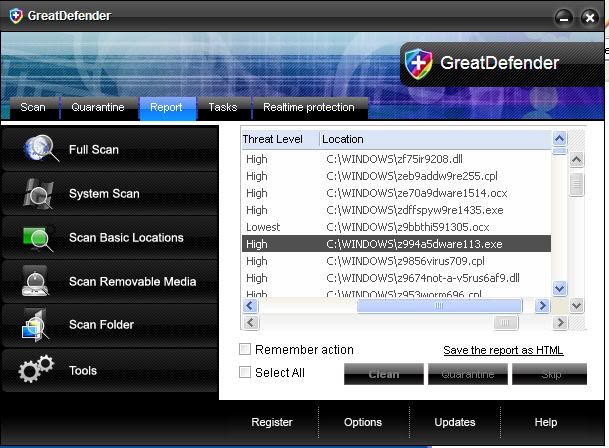
Fake Alert : GreatDefender
a-squared 4.5.0.43 2009.12.30 -
AhnLab-V3 5.0.0.2 2009.12.29 -
AntiVir 7.9.1.122 2009.12.30 -
Antiy-AVL 2.0.3.7 2009.12.30 -
Authentium 5.2.0.5 2009.12.30 -
Avast 4.8.1351.0 2009.12.30 -
AVG 8.5.0.430 2009.12.30 -
BitDefender 7.2 2009.12.30 -
CAT-QuickHeal 10.00 2009.12.30 -
ClamAV 0.94.1 2009.12.30 -
Comodo 3414 2009.12.30 -
DrWeb 5.0.1.12222 2009.12.30 -
eSafe 7.0.17.0 2009.12.29 -
eTrust-Vet 35.1.7206 2009.12.30 -
F-Prot 4.5.1.85 2009.12.30 -
F-Secure 9.0.15370.0 2009.12.30 -
Fortinet 4.0.14.0 2009.12.30 -
GData 19 2009.12.30 -
Ikarus T3.1.1.79.0 2009.12.30 -
Jiangmin 13.0.900 2009.12.30 -
K7AntiVirus 7.10.932 2009.12.28 -
Kaspersky 7.0.0.125 2009.12.30 -
McAfee 5846 2009.12.29 FakeAlert-JM
McAfee+Artemis 5846 2009.12.29 FakeAlert-JM
McAfee-GW-Edition 6.8.5 2009.12.30 -
Microsoft 1.5302 2009.12.30 -
NOD32 4728 2009.12.30 -
Norman 6.04.03 2009.12.30 W32/FakeAV.JFW
nProtect 2009.1.8.0 2009.12.30 -
Panda 10.0.2.2 2009.12.30 -
PCTools 7.0.3.5 2009.12.30 -
Prevx 3.0 2009.12.30 -
Rising 22.28.02.04 2009.12.30 -
Sophos 4.49.0 2009.12.30 -
Sunbelt 3.2.1858.2 2009.12.30 -
Symantec 1.4.4.12 2009.12.30 -
TheHacker 6.5.0.3.121 2009.12.30 -
TrendMicro 9.120.0.1004 2009.12.30 -
VBA32 3.12.12.1 2009.12.30 -
ViRobot 2009.12.30.2116 2009.12.30 -
VirusBuster 5.0.21.0 2009.12.29 -
==================================================
Files CreatedCommonDesktopDir%\GreatDefender.lnk
%CommonPrograms%\GreatDefender\1 GreatDefender.lnk
%CommonPrograms%\GreatDefender\2 Homepage.lnk
%CommonPrograms%\GreatDefender\3 Uninstall.lnk
%Temp%\nsa3.tmp\nsProcess.dll
%ProgramFiles%\GreatDefender Software\GreatDefender\GreatDefender.exe
%ProgramFiles%\GreatDefender Software\GreatDefender\uninstall.exe
%Windir%\10501sp5mbot2z19.dll
%Windir%\10550zor53ad9.exe
%Windir%\110z0s9y3d5.ocx
%Windir%\11153troj5z89.ocx
%Windir%\114859orm5e4z.exe
%Windir%\115fspzwar92928.ocx
%Windir%\115tzief9853.ocx
%Windir%\1165stealz629.exe
%Windir%\11sza95ot111.bin
%Windir%\122689r5j5zb.ocx
%Windir%\12558ha9ktool4z05.bin
%Windir%\126z1wo5m98f.ocx
%Windir%\130595zef3243.exe
%Windir%\13827tr9jza5.exe
%Windir%\13936sp5zbo9755.ocx
%Windir%\1494not-a-59rzs3c.exe
%Windir%\1503a5dwa9e195z.ocx
%Windir%\15080not5a-vzru969f.dll
%Windir%\15429ir10z.exe
%Windir%\15459z5rus18f.exe
%Windir%\15615vi9uz6aa5.dll
%Windir%\15728z9oj559.bin
%Windir%\15739ir83z.cpl
%Windir%\1594zhackt9ol6655.bin
%Windir%\159z9worm49.exe
%Windir%\15ddsparse2z97.bin
%Windir%\15z065ro95e9.bin
%Windir%\15z48sp9601.exe
%Windir%\15z49virus399.cpl
%Windir%\16982zor595c.ocx
%Windir%\16z64sp95245.bin
%Windir%\174515py917z.dll
%Windir%\17614trojzc95.ocx
%Windir%\17752troj99z.exe
%Windir%\1795vizu5628.ocx
%Windir%\17fzspyware29375.exe
%Windir%\18964spam5ot5az.bin
%Windir%\18ea95zrse2651.ocx
%Windir%\1950not5z-vi9us670.exe
%Windir%\196z1t9oj559.cpl
%Windir%\19865sp5mbot5az.exe
%Windir%\1991059rzs50b.dll
%Windir%\19950tz9j18d.dll
%Windir%\19z53s5am9ot335.bin
%Windir%\19z95h9ck5ool73.bin
%Windir%\1b9thiez1533.cpl
%Windir%\1cb3sparsez295.bin
%Windir%\1d25tzreat29018.bin
%Windir%\1d93addwzr52565.exe
%Windir%\1ez9do5nl9ader2545.exe
%Windir%\20959oz-a-virus1535.exe
%Windir%\20b3baczdo5r14649.dll
%Windir%\21139zp5mbot648.cpl
%Windir%\21815not-9-virus57z.bin
%Windir%\21f5th9eat29945z.dll
%Windir%\21z905ir9s163.cpl
%Windir%\222not-a-z5rus794.ocx
%Windir%\22714hackt9ol5z5.exe
%Windir%\2295ad9war538z.exe
%Windir%\230159py79z.cpl
%Windir%\23199sp5mzot2a2.exe
%Windir%\239105izu93a4.exe
%Windir%\23952spy585z.dll
%Windir%\24291not-a-v5zus2c5.cpl
%Windir%\249765orm5z4.dll
%Windir%\253625pzmbo929e.ocx
%Windir%\25514h5cktool49bz.exe
%Windir%\25531szambot199.ocx
%Windir%\25532spy96z.dll
%Windir%\255faddwz9e31715.ocx
%Windir%\255z0wor931b.dll
%Windir%\25713wo9z5c6.ocx
%Windir%\2594steaz5279.exe
%Windir%\25999no9-a-virusz35.dll
%Windir%\259bdowz9oader1051.cpl
%Windir%\25b9th9eatz9391.exe
%Windir%\25c2do9nloaderz054.bin
%Windir%\25d69hizf1155.exe
%Windir%\25s9yzfa5.cpl
%Windir%\2604addz9re5193.bin
%Windir%\26566h9ck5ool199z.bin
%Windir%\265zpambot109.ocx
%Windir%\269095zrus573.cpl
%Windir%\275679pambotz15.exe
%Windir%\277359pz540.ocx
%Windir%\28235zpy5b9.exe
%Windir%\28522tro975z.cpl
%Windir%\286dzt9al1615.ocx
%Windir%\288865ot-a-vizus2c9.ocx
%Windir%\29154haczt5ol2bd.exe
%CommonDesktopDir% = C:\Documents and Settings\All Users\Desktop
%CommonPrograms% = C:\Documents and Settings\All Users\Start Menu\Programs
%Windir% = C:\Wondows
Registry Modifications
Keys Added
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GreatDefender
HKLM\SOFTWARE\GreatDefender
Values Added
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\
cf = ""
tr = ""
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\GreatDefender\
DisplayName = "GreatDefender"
UninstallString = ""%ProgramFiles%\GreatDefender Software\GreatDefender\uninstall.exe""
NoModify = 0x00000001
NoRepair = 0x00000001
HKLM\SOFTWARE\GreatDefender\
Lang = "English"
Install_Dir = "%ProgramFiles%\GreatDefender Software\GreatDefender"
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\
GreatDefender = %ProgramFiles%\GreatDefender Software\GreatDefender\GreatDefender.exe
==================================================
วิธีกำจัด /แก้ : Fake Alert : GreatDefender
==================================================
Download Fix Tool :
Download : Malware byte' AntiMalware