*ผมไม่มีตัวอย่างไฟล์ Trojan Anti AV ตัวนี้ นะครับ
อยากได้ เหมือนกันครับ ผมเจอ link ที่ Download Trojan ตัวนี้ แต่ Download ไม่ได้*
เมื่อติดแล้ว เจ้าโทรจันตัวนี้ จะไป uninstall ตัวโปรแกรม Antivirus ตัวเิดิมออก
แล้วติดตั้ง ตัวเอง โดย เลียนแบบ icon ของ antivirus ยี่ห้อดังหลายตัว เช่น
KAV, ESET, Outpost, Comodo, Agava, Avast, McAfee, Avira, Norton, DrWeb, MSE, MSD, AVG, Panda
-----------------------------------------------------------------------
Flash-Player.exe
MD5 : 38acffb9479dbfe7869fa46b9f8c40a8
SHA1 : faabde662b668c6c82c347a75cc439b771919773
MD5 : bfe737620506583c7cddd18a71479b1c
SHA1 : 81e5a20461980bc70523812aca5a05edd873f81e
...
| Antivirus | Version | Last update | Result |
|---|---|---|---|
| AhnLab-V3 | 2011.07.30.00 | 2011.07.29 | Win-Trojan/Vkont.1201664 |
| AntiVir | 7.11.12.167 | 2011.07.29 | BDS/Bafruz.B |
| Antiy-AVL | 2.0.3.7 | 2011.07.29 | Trojan/win32.agent.gen |
| Avast | 4.8.1351.0 | 2011.07.29 | Win32:Malware-gen |
| Avast5 | 5.0.677.0 | 2011.07.29 | Win32:Malware-gen |
| AVG | 10.0.0.1190 | 2011.07.29 | SHeur3.CLIY |
| BitDefender | 7.2 | 2011.07.29 | Trojan.Agent.ASAI |
| CAT-QuickHeal | 11.00 | 2011.07.29 | - |
| ClamAV | 0.97.0.0 | 2011.07.29 | - |
| Commtouch | 5.3.2.6 | 2011.07.29 | - |
| Comodo | 9557 | 2011.07.29 | Heur.Suspicious |
| DrWeb | 5.0.2.03300 | 2011.07.29 | Trojan.VkBase.73 |
| Emsisoft | 5.1.0.8 | 2011.07.29 | Backdoor.Win32.Bafruz!IK |
| eSafe | 7.0.17.0 | 2011.07.27 | - |
| eTrust-Vet | 36.1.8472 | 2011.07.29 | - |
| F-Prot | 4.6.2.117 | 2011.07.29 | - |
| F-Secure | 9.0.16440.0 | 2011.07.29 | Trojan.Agent.ASAI |
| Fortinet | 4.2.257.0 | 2011.07.29 | - |
| GData | 22 | 2011.07.29 | Trojan.Agent.ASAI |
| Ikarus | T3.1.1.104.0 | 2011.07.29 | Backdoor.Win32.Bafruz |
| Jiangmin | 13.0.900 | 2011.07.29 | Trojan/AntiAV.btb |
| K7AntiVirus | 9.109.4961 | 2011.07.29 | Trojan |
| Kaspersky | 9.0.0.837 | 2011.07.29 | Trojan.Win32.AntiAV.oax |
| McAfee | 5.400.0.1158 | 2011.07.29 | FakeAlert-SecurityAntivirus |
| McAfee-GW-Edition | 2010.1D | 2011.07.29 | FakeAlert-SecurityAntivirus |
| Microsoft | 1.7104 | 2011.07.29 | Backdoor:Win32/Bafruz.B |
| NOD32 | 6335 | 2011.07.29 | Win32/Delf.QCZ |
| Norman | 6.07.10 | 2011.07.29 | Delf.FHUF |
| nProtect | 2011-07-29.02 | 2011.07.29 | Trojan/W32.AntiAV.1201664 |
| Panda | 10.0.3.5 | 2011.07.29 | Trj/CI.A |
| PCTools | 8.0.0.5 | 2011.07.29 | Trojan.Generic |
| Prevx | 3.0 | 2011.07.29 | - |
| Rising | 23.68.04.03 | 2011.07.29 | Suspicious |
| Sophos | 4.67.0 | 2011.07.29 | Mal/Generic-L |
| SUPERAntiSpyware | 4.40.0.1006 | 2011.07.29 | - |
| Symantec | 20111.1.0.186 | 2011.07.29 | Trojan Horse |
| TheHacker | 6.7.0.1.264 | 2011.07.28 | - |
| TrendMicro | 9.200.0.1012 | 2011.07.29 | - |
| TrendMicro-HouseCall | 9.200.0.1012 | 2011.07.29 | TROJ_ANTIAV.CW |
| VBA32 | 3.12.16.4 | 2011.07.29 | - |
| VIPRE | 9999 | 2011.07.29 | Trojan.Win32.Generic!BT |
| ViRobot | 2011.7.29.4595 | 2011.07.29 | Dropper.Agent.1201664 |
| VirusBuster | 14.0.145.2 | 2011.07.29 | Trojan.AntiAV!/9aazmSPFg0 |
...
File Added
%Windir%\sysdriver32.exe
%Windir%\sysdriver32_.exe
%Windir%\Temp\2105191.exe
%Windir%\loader2.exe_ok
%Windir%\services32.exe
%Windir%\update.1\svchost.exe
%Temp%\141329.exe
%Temp%\4621672.exe
%Temp%\1962094.bat
%Temp%\40296133.bat
([number].exe or .bat)
%Profiles%\LocalService\Start Menu
%Profiles%\LocalService\Start Menu\Programs
%Windir%\update.1
%Temp% = C:\Documents and Settings\[UserName]\Local Settings\Temp
%Profiles% = C:\Documents and Settings
%Windir% = C:\Windows or C:\Winnt
Registry Modifications
Keys added
HKLM\SOFTWARE\services32.exe
HKLM\SOFTWARE\sysdriver32.exe
HKLM\SOFTWARE\systeminfog
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\wxpdrivers
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Network\wxpdrivers
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000\Control
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Security
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Enum
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Security
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Enum
HKLM\SYSTEM\ControlSet002\Control\SafeBoot\Minimal\wxpdrivers
HKLM\SYSTEM\ControlSet002\Control\SafeBoot\Network\wxpdrivers
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\wxpdrivers
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\wxpdrivers
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000\Control
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Security
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Enum
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Security
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Enum
HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
HKCU\Software\Classes\Software\Microsoft\Windows\CurrentVersion\Policies
HKCU\Software\Classes\Software\Microsoft\Windows\CurrentVersion\Policies\Associations
Values added
HKLM\SOFTWARE\Microsoft\Security Center
DisableThumbnailCache = 0x00000001
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
EnableLUA = 0x00000000
EnableSecureUIAPaths = 0x00000000
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
wxpdrv = "%Windir%\update.1\svchost.exe"
4621672.exe = ""%Temp%\4621672.exe""
sysdriver32.exe = ""%Windir%\sysdriver32.exe" rezerv"
sysdriver32_.exe = ""%Windir%\sysdriver32_.exe" rezerv"
141329.exe = ""%Temp%\141329.exe""
2105191.exe = ""%Windir%\TEMP\2105191.exe""
HKLM\SOFTWARE\services32.exe
close = "0"
ver = "3.14"
HKLM\SOFTWARE\sysdriver32.exe
time = "3520950973"
ver = "1.37"
path = "%Windir%\"
HKLM\SOFTWARE\systeminfog
ip_list = "188.231.226.178
[78.153.109.112]
95.158.189.4 = 46.118.28.239
[24.50.254.65]
77.122.73.101 = 82.208.135.110
[31.63.210.89]
79.116.55.111 = 217.129.77.109
[46.0.33.186]
190.213.221.57 = 94.112.230.65
[79.121.115.162]
84.201.207.27 = 109.160.118.175
[46.16]
HKLM\SOFTWARE\systeminfog = ip_list_time
["3520950927"]
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\wxpdrivers = (Default)
["Service"]
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Network\wxpdrivers = (Default)
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control = *NewlyCreated*
HKLM\SYSTEM\ControlSet002\Control\SafeBoot\Network\wxpdrivers = (Default)
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal\wxpdrivers = (Default)
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\wxpdrivers = (Default)
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control = *NewlyCreated*
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Service
[0x00000000]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control = ActiveService
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Class
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000\Control = ActiveService
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = Class
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = ImagePath
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000\Control = ActiveService
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Class
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000\Control = ActiveService
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = Class
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers = ImagePath
["srvsysdriver32"]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Service
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Legacy
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32 = NextInstance
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Service
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = Legacy
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32 = NextInstance
[0x00000001]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = ConfigFlags
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000\Control = *NewlyCreated*
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = ConfigFlags
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Enum = 0
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Enum = NextInstance
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Security = Security
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32 = ImagePath
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Enum = NextInstance
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Security = Security
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = ConfigFlags
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000\Control = *NewlyCreated*
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = ConfigFlags
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Enum = 0
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Enum = NextInstance
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Security = Security
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32 = ImagePath
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Enum = NextInstance
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Security = Security
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = Service
["LegacyDriver"]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = ClassGUID
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = ClassGUID
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = ClassGUID
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = ClassGUID
["{8ECC055D-047F-11D1-A537-0000F8753ED1}"]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = DeviceDesc
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = DeviceDesc
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_SRVSYSDRIVER32\0000 = DeviceDesc
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = DeviceDesc
["wxpdrivers"]
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = Service
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS\0000 = Legacy
HKLM\SYSTEM\ControlSet001\Enum\Root\LEGACY_WXPDRIVERS = NextInstance
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = ObjectName
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = Service
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS\0000 = Legacy
HKLM\SYSTEM\CurrentControlSet\Enum\Root\LEGACY_WXPDRIVERS = NextInstance
["Root\LEGACY_SRVSYSDRIVER32\0000"]
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32\Enum = Count
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32\Enum = Count
[01 00 14 80 90 00 00 00 9C 00 00 00 14 00 00 00 30 00 00 00 02 00 1C 00 01 00 00 00 02 80 14 00 FF 01 0F 00 01 01 00 00 00 00 00 01 00 00 00 00 02 00 60 00 04 00 00 00 00 00 14 00 FD 01 02 00 01 01 00 00 00 00 00 05 12 00 00 00 00 00 18 00 FF 01 0F 0]
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32 = Type
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = Type
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32 = Type
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers = Type
[0x00000010]
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32 = Start
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = Start
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32 = Start
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers = Start
[0x00000002]
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32 = ErrorControl
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = ErrorControl
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32 = ErrorControl
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers = ErrorControl
["%Windir%\sysdriver32.exe srv"]
HKLM\SYSTEM\ControlSet001\Services\srvsysdriver32 = ObjectName
HKLM\SYSTEM\CurrentControlSet\Services\srvsysdriver32 = ObjectName
["LocalSystem"]
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Enum = 0
HKLM\SYSTEM\ControlSet002\Control\SafeBoot\Minimal\wxpdrivers = (Default)
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Enum = 0
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Security = Security
["Root\LEGACY_WXPDRIVERS\0000"]
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers\Enum = Count
HKLM\SYSTEM\CurrentControlSet\Services\wxpdrivers\Enum = Count
["%Windir%\update.1\svchost.exe srv"]
HKLM\SYSTEM\ControlSet001\Services\wxpdrivers = DisplayName
Values modified
HKLM\SOFTWARE\Microsoft\Security Center
FirewallOverride =
HKLM\SYSTEM\ControlSet001\Control\SafeBoot
AlternateShell =
HKLM\SYSTEM\ControlSet001\Control\ServiceCurrent
(Default) =
HKLM\SYSTEM\ControlSet002\Control\SafeBoot
AlternateShell =
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot
AlternateShell =
HKLM\SYSTEM\CurrentControlSet\Control\ServiceCurrent
(Default) =
HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
Programs =
...
อาการหลังติด Trojan Anti AV
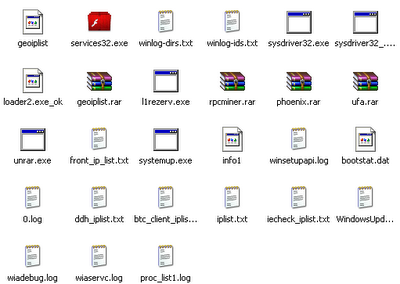
ตัวอย่าง ไฟล์ที่ trojan สร้างไว้
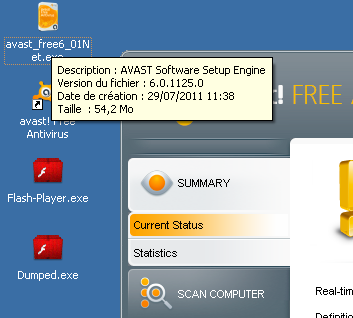
ตัวอย่้าง Avast ก่อนติดตั้ง Fake
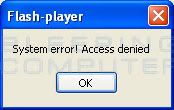
icon หลังติดตั้ง Trojan
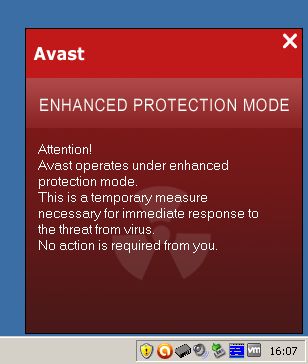
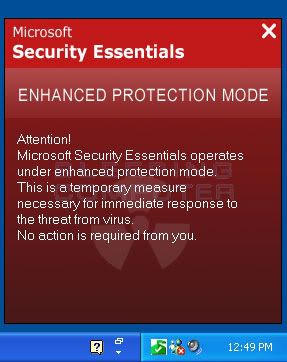
เมื่อลอง click ที่ icon จะพบข้อความดังภาพ
avast
Microsoft Security Essentials
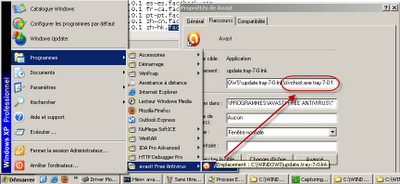
เมื่อลองเลือก Shortcut program จะพบว่าไม่ได้ชี้ไปยัง Antivirus แต่ชี้ไปที่ svchost.exe
ที่ไม่ใช้ไฟล์ของ ระบบ Windows
Icon ที่ Trojan ใช้ เลียนแบบ
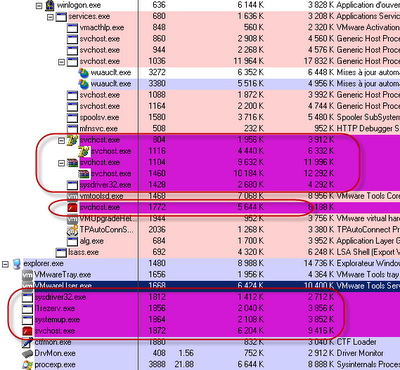
ถ้าลองเปิดด้วยโปรแกรม Process Exlorer จะพบ Process ของ Trojan ที่ Run อยู่
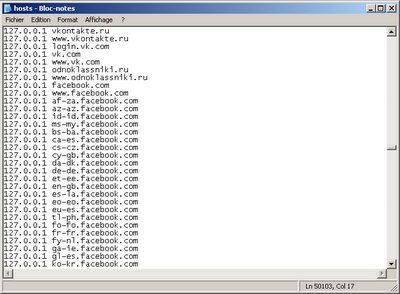
Trojan แก้ไขค่าในไฟล์ hosts
........................................................................................................................
วิธีแก้ไข / กำจัด : Trojan Anti AV (Fake AV)
........................................................................................................................
Download :Rkill.com , TDSS Killer ,
ดูรายละเีอียด hosts จาก link นี้ครับ http://winhelp2002.mvps.org/hosts.htm
1. Run Rkill.com
2. Run TDSSKiller
2. ติดตั้ง Kaspersky Virus Remove Tool (2010 หรือ 2011) แล้ว Scan
หรืออาจใช้ malwarebytes' anti-malware ก็ได้ครับ
3. แก้ไข Hosts โดย Run ไฟล์ MVP.bat หรืออาจใช้ HostsXpert แ้ก้ไข Hosts
4. ลองเปิด HijackThis ขึ้นมา หาบรรทัดเหล่านี้(ถ้ามี)
โดยตัวเลขอาจไม่ตรงตามนี้ [number].exe แต่ให้สังเกตุที่ path จาก %temp%
O4 - HKLM\..\Run: [wxpdrv] "%Windir%\update.1\svchost.exe"
O4 - HKLM\..\Run: [4621672.exe] "%Temp%\4621672.exe"
O4 - HKLM\..\Run: [sysdriver32.exe] "%Windir%\sysdriver32.exe" rezerv"
O4 - HKLM\..\Run: [sysdriver32_.exe] "%Windir%\sysdriver32_.exe" rezerv"
O4 - HKLM\..\Run: [141329.exe] "%Temp%\141329.exe"
O4 - HKLM\..\Run: [2105191.exe] "%Windir%\Temp\2105191.exe"
5. Restart
ขอขอบคุณแหล่งข้อมูลอ้างอิง



ไม่มีความคิดเห็น:
แสดงความคิดเห็น