ESET uncovers another porn clicker on Google Play

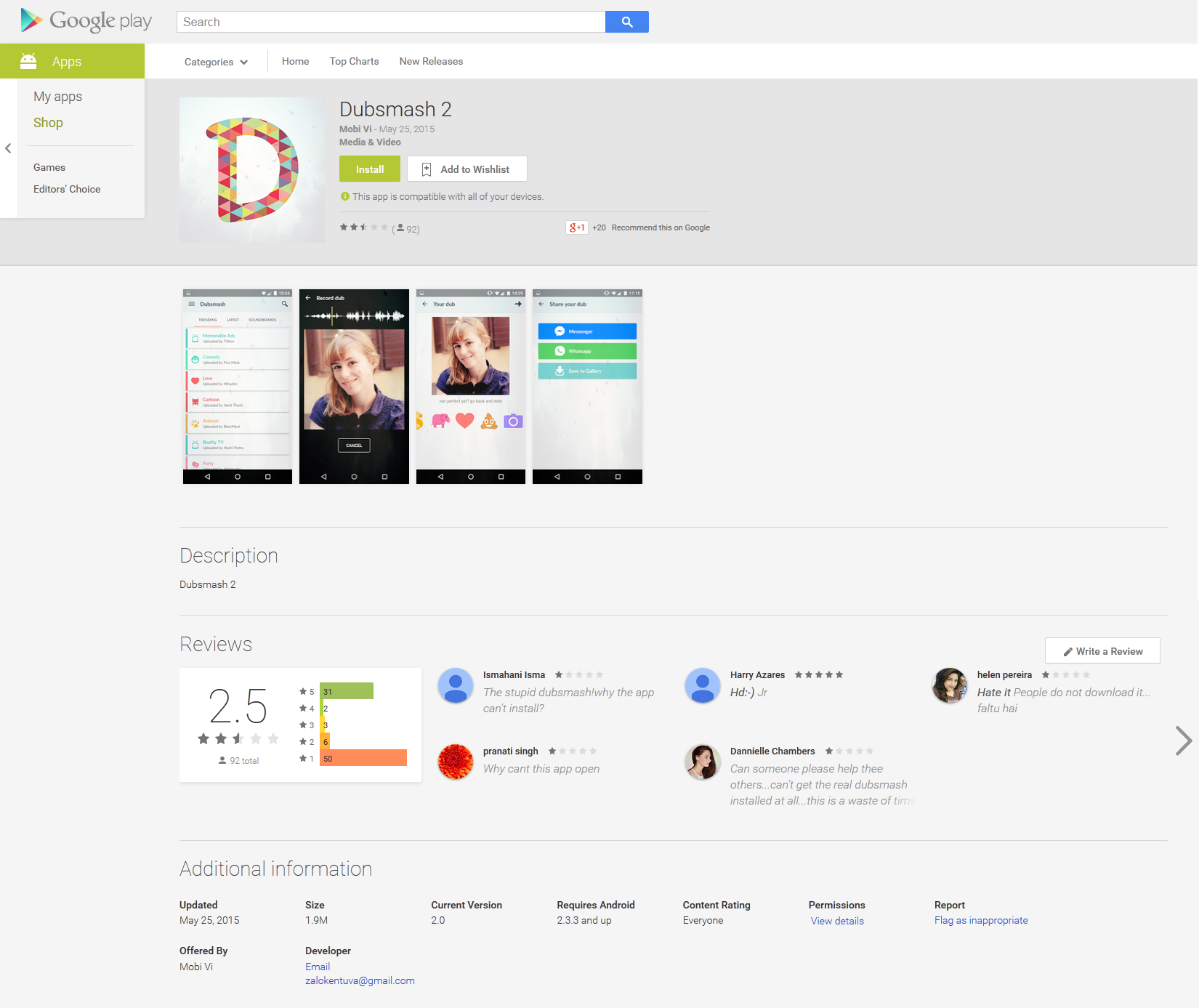
Recently, Avast researchers discovered the Trojan porn clicker uploaded to Google Play Store and posing as “Dubsmash 2”.
This clicker pretended to be an official application, and was
downloaded more than 100,000 times. While the click fraud activity did
not cause direct harm to the victims such as stealing credentials, it
does generate a lot of internet traffic and may cause high data charges
for victims that have a restricted data plan, leaving them with high
cellphone bills at the end of the month.
Less than a month later, ESET researchers
discovered that a plethora of variants of this same fake Dubsmash
application found their way on to the official Google Play, showing the
very same icons and preview pictures.
While this threat is entirely different from the one we documented last week, both cases are similar in the sense that they managed to get into the Google Play Store when they should have been rejected.
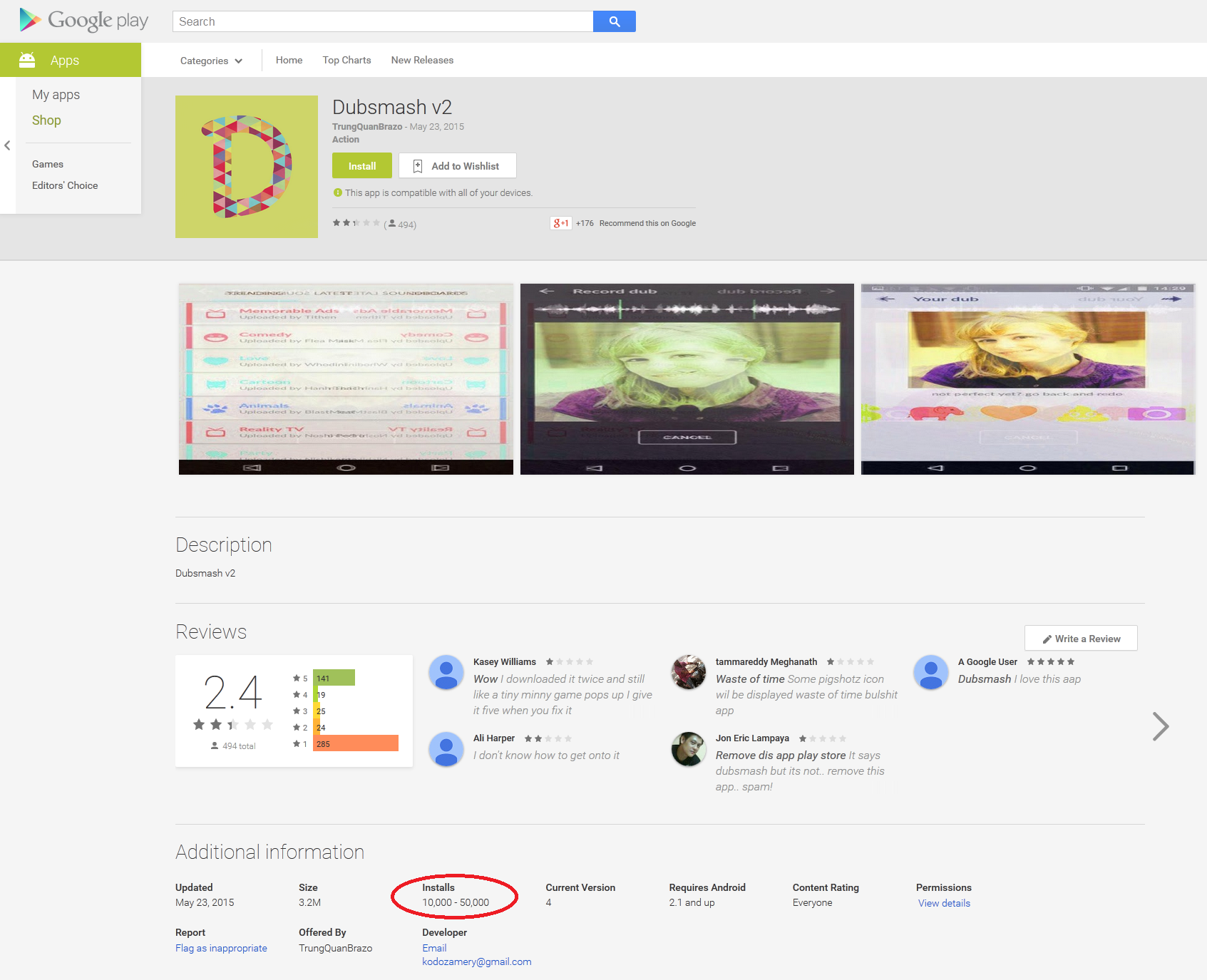
The latest Dubsmash 2 Trojan was uploaded to
Play Store on May 20, 2015 and pulled on May 22, 2015. In the two days
during that it was available for download, it was downloaded more than
5,000 times. The malware once again used a clicker technique identical
to that used in its earlier version.
The author of the malware didn’t wait too long
before uploading another version of the porn clicker to Google Play on
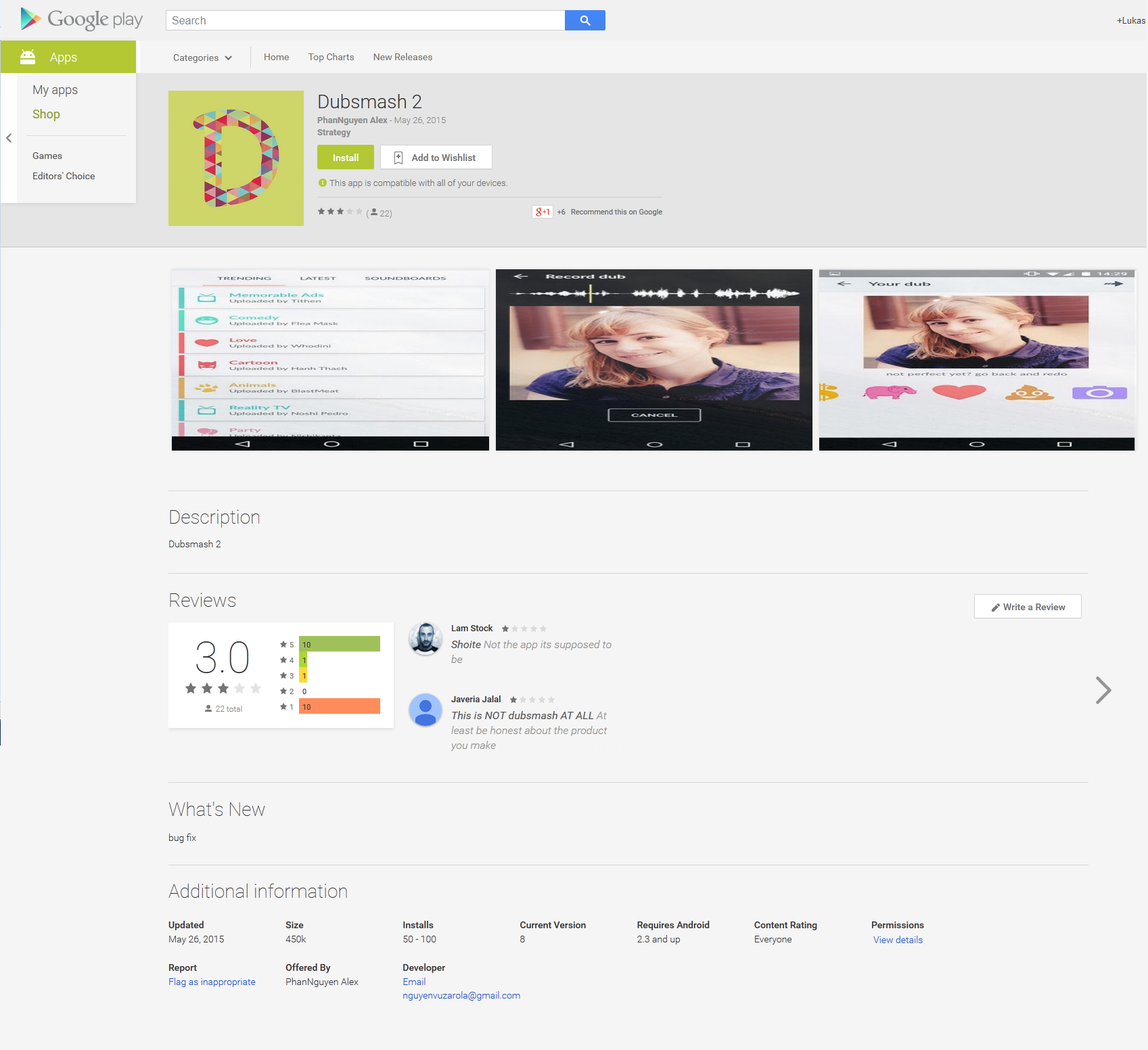
May 23, 2015, passed off as Dubsmash v2. After three days the application had been downloaded more than ten of thousands of times. On May 25, 2015 and on May 26 2015 Dubsmash 2
was uploaded to the Play Store for the fourth and fifth time with the
same malicious code implemented. It’s very rare for malware to be
uploaded to official Play Store with the same functionality so many
times over such a short period.
ESET security software detects this threat as Android/Clicker Trojan. The fake applications were quickly removed from Play Store after we notified Google.
After further research we discovered that these
four applications were not the only Dubsmash 2 applications uploaded to
the Google Play Store. We found another four applications that were
removed from the Play Store in the past. ESET identified nine Trojan
Clicker applications altogether that were made available for download,
disguised as fake Dubsmash 2 applications.
Analysis
After installation, the user will not find any
new Dubsmash icon on the device. The newly installed app’s icon or name
has nothing in common with the real Dubsmash application. Mostly it
pretends to be a simple arcade game or system application. After
startup, the application hide its launching icon, but it is still
constantly running in the background, accessing porn pages to generate
revenue via click fraud.
Malicious activity is triggered when the device
changes its connection. It’s not difficult to get the server URL
address, as the app developer did not encrypt URLs this time. The server
URL can be found in the code in plaintext. But there is one interesting
change from the last version. Malicious code will not be executed if
anti-virus software is installed on the device. The Trojan checks
installed applications, based on package names, against the names of 16
anti-virus vendors. Package names are dynamically requested from server
over HTTP. Package names can be easily updated to add other anti-malware
applications. When the Trojan is installed it may not yet be detected
by all AV solutions, but in many cases AV vendors can block URLs on
request if they are found to be malicious. In one case the Trojan uses
the server to communicate with as in its earlier version. It’s very
suspicious when the user is warned that his device is trying to request
data from a server that has already been blocked. At this point, the
user may be alarmed to find that something suspicious is going on.
Package Name
|
|---|
| com.eset.ems2.gp |
| com.kms.free |
| com.avast.android.mobilesecurity |
| com.symantec.mobilesecurity |
| com.antivirus |
| com.drweb |
| com.cleanmaster.mguard |
| com.cleanmaster.security |
| com.avira.android |
| com.wsandroid.suite |
| com.drweb.pro |
| org.antivirus |
| com.s.antivirus |
| jp.naver.lineantivirus.android |
| org.antivirus.tablet |
| org.antivirus.tcl.plugin.trial_to_pro |
If none of these applications are installed
then Dubsmash 2’s true functionality is initiated. The Trojan will
demand porn links from its server. These links will be loaded every 60
seconds into WebView inside an invisible window, with a random clicking
pattern applied.
Conclusion
It looks as if the official Play Store has
still some weak spots, given that the same malicious applications were
uploaded and offered to more than ten of thousands of users for the
fourth time in just a month. The developer misused the name of a
popular, for his own financial gain. We advise users to read reviews
even when the application is not requesting any harmful or suspicious
permissions.
More information
Package name
|
MD5
|
ESET Detection name
|
|---|---|---|
| com.mym.gms | BC72AD89E02C5FAA8FD84EBE9BF9E867 | Android/Clicker.M |
| com.jet.war | 8788B7C60BC9021A5F6162014D7BD1A6 | Android/Clicker.L |
| com.lh.screens | A2CCD03A1997F86FB06BD1B21556C30F | Android/Clicker.M |
| com.jet.sman | 6E20146EB52AEA41DB458F494C3ED3E6 | Android/Clicker.J |
Author Lukas Stefanko, ESET
ที่มา :www.welivesecurity.com






ไม่มีความคิดเห็น:
แสดงความคิดเห็น