Emsisoft CTO/researcher Fabian Wosar has created a decrypter for the newly discovered OpenToYou ransomware that will allow infected victims to recover encrypted files without needing to pay a ransom.
The ransomware’s name comes from the email address at which the crook wants victims to reach out (opentoyou@india.com), and by the file extension appended to each encrypted file (.-opentoyou@india.com).
OpenToYou infection process
When it first infects a computer, the OpenToYou ransomware will create a password string, use SHA-1 to derive an encryption key from the password, which it then uses to encrypt the victim’s files with the RC4 algorithm.
The ransomware targets 242 file types for encryption. The following file extensions are targeted:
*.3ds,*.3fr,*.4db,*.7z,*.7zip,*.accdb,*.accdt,*.aes,
*.ai,*.apk,*.arch00,*.arj,*.arw, *.asset,*.avi,*.bar,*.bay,*.bc6,*.bc7,*.big,*.bik,
*.bkf,*.bkp,*.blob,*.bpw,*.bsa, *.cas,*.cdr,*.cer,*.cfr,*.cr2,*.crp,*.crt,*.crw,
*.css,*.csv,*.d3dbsp,*.das,*.dazip, *.db0,*.dba,*.dbf,*.dbx,*.dcr,*.der,*.desc,*.dmp,
*.dng,*.doc,*.docm,*.docx,*.dot, *.dotm,*.dotx,*.dwfx,*.dwg,*.dwk,*.dxf,*.dxg,*.eml,
*.epk,*.eps,*.erf,*.esm,*.ff,*.flv, *.forge,*.fos,*.fpk,*.fsh,*.gdb,*.gho,*.gpg,*.gxk,
*.hkdb,*.hkx,*.hplg,*.hvpl,*.ibank, *.icxs,*.idx,*.ifx,*.indd,*.iso,*.itdb,*.itl,*.itm,
*.iwd,*.iwi,*.jpe,*.jpeg,*.jpg,*.js, *.kdb,*.kdbx,*.kdc,*.key,*.kf,*.ksd,*.layout,*.lbf,
*.litemod,*.lrf,*.ltx,*.lvl,*.m2, *.m3u,*.m4a,*.map,*.max,*.mcmeta,*.mdb,*.mdbackup,
*.mddata,*.mdf,*.mef,*.menu,*.mlx, *.mov,*.mp3,*.mp4,*.mpd,*.mpp,*.mpqge,*.mrwref,
*.myo,*.nba,*.nbf,*.ncf,*.nrw,*.nsf, *.ntl,*.nv2,*.odb,*.odc,*.odm,*.odp,*.ods,*.odt,
*.ofx,*.orf,*.p12,*.p7b,*.p7c,*.pak, *.pdb,*.pdd,*.pdf,*.pef,*.pem,*.pfx,*.pgp,*.pkpass,
*.png,*.ppj,*.pps,*.ppsx,*.ppt, *.pptm,*.pptx,*.prproj,*.psd,*.psk,*.pst,*.psw,*.ptx,
*.py,*.qba,*.qbb,*.qbo,*.qbw, *.qdf,*.qfx,*.qic,*.qif,*.raf,*.rar,*.raw,*.rb,*.re4,
*.rgss3a,*.rim,*.rofl,*.rtf, *.rw2,*.rwl,*.saj,*.sav,*.sb,*.sdf,*.sid,*.sidd,
*.sidn,*.sie,*.sis,*.sko,*.slm,*.snx, *.sql,*.sr2,*.srf,*.srw,*.sum,*.svg,*.sxc,*.syncdb,
*.t12,*.t13,*.tar,*.tax,*.tbl, *.tib,*.tor,*.txt,*.upk,*.vcf,*.vdf,*.vfs0,*.vpk,
*.vpp_pc,*.vtf,*.w3x,*.wallet,*.wb2, *.wdb,*.wma,*.wmo,*.wmv,*.wotreplay,*.wpd,*.wps,
*.x3f,*.xf,*.xlk,*.xls,*.xlsb,*.xlsm, *.xlsx,*.xml,*.xxx,*.zip,*.ztmp
As a side note, OpenToYou also encrypts files without a file extension.
The ransomware will lock files on all drives, with the exemption of the following folders:
C:$Recycle.Bin C:Logs C:UsersAll Users C:Windows C:ProgramData C:Program Files C:Program Files (x86) C:nvidia C:intel C:Boot C:bootmgr C:PerfLogs C:Drivers C:MSOCache C:Program instal %USERPROFILE%AppData
Unfortunately, this exemptions list contains an error. “C:bootmgr” is not a folder, but a file.
This slip-up on the part of OpenToYou’s author leads to situations where the ransomware encrypts the boot loader “bootmgr” on Windows workstations that use the MBR to boot. This leaves the victim’s computer in the unfortunate situation of not being able to boot the next time they restart their PC.
After the encryption process ends, the ransomware will replace the user’s desktop wallpaper with the following image:
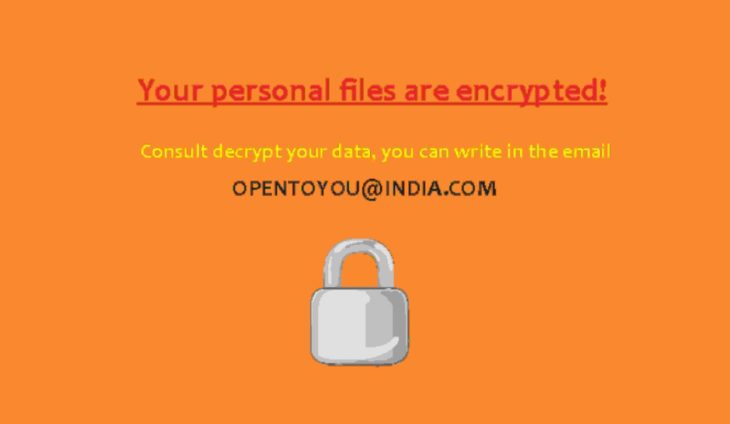
At the same time, OpenToYou drops a file named !!!.txt on the user’s Desktop. This file contains a written version of the ransom note, as reproduced below:
Your files are encrypted!
To decrypt write on email – opentoyou@india.com
Identification key – 5E1C0884
The number “5E1C0884” from the ransom note above is the victim’s ID, which he must send to the ransomware author via email. This ID is each computer’s C: drive’s volume serial number.
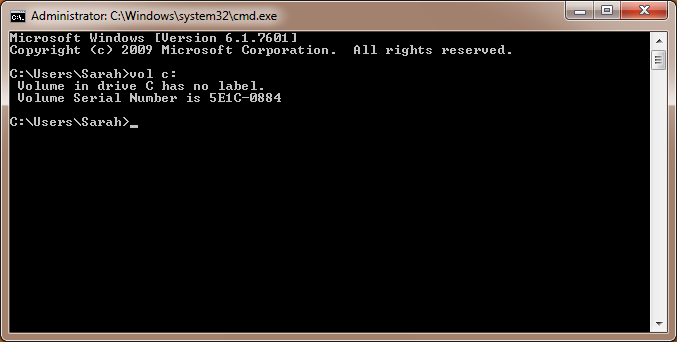
At the time of writing, the ransomware appears to be under development. The reason behind this assumption is the ransomware creates a folder named “C:Logs” to store temporary files and debug data.
This folder’s content is always the same, and its presence can be used to detect OpenToYou ransomware infections in their early stages.
C:Logs1.bmp [the desktop wallpaper image] C:Logs1.jpg [the desktop wallpaper image] C:LogsAllFilesList.ini C:LogsLog.ansi.txt C:LogsLog.UTF-16LE.txt
Victims affected by this ransomware can recover their data using the Emsisoft OpenToYou Decrypter, which is available for download on our site.
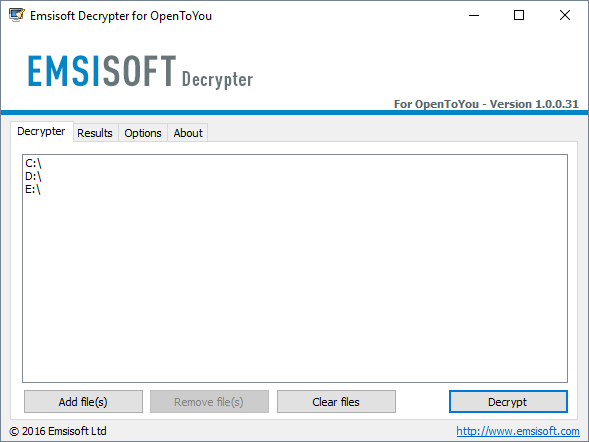
It is not uncommon to see in-dev ransomware being analysed and decrypted even before it’s delivered to users via spam or malvertising campaigns. If you’ve been infected by a version of this ransomware, don’t hesitate to reach out to Emsisoft researchers for help.
Users employing Emsisoft Anti-Malware or Emsisoft Internet Security have been proactively protected from this threat by Emsisoft’s Behavior Blocker technology:
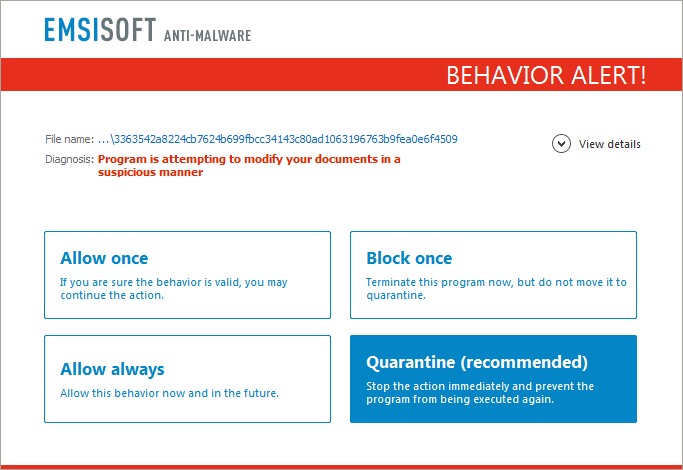
This blog post is based on the OpenToYou ransomware sample with the following SHA-256 hash: 3363542a8224cb7624b699fbcc34143c80ad1063196763b9fea0e6f45091454c.
Credit : blog.emsisoft.comhttps://blog.emsisoft.com/en/25673/emsisoft-releases-free-decrypter-for-opentoyou-ransomware/



ไม่มีความคิดเห็น:
แสดงความคิดเห็น