Security Alert: New Dharma Ransomware Strains Alarmingly Go Undetected By Antivirus Engines
At least four new strains appeared recently . We even discovered one that goes undetected by almost all the antivirus engines on the market.
Dharma ransomware is one of the oldest ransomware families in existence and yet it still wreaks havoc, undetected by security solutions.
October and November saw the appearance of at least four new strains.
We discovered one that goes undetected by almost all the antivirus engines on the market.
If this trend continues, users who rely on antivirus alone for ransomware protection will be at risk of losing their data forever – there is no free decryption tool for the new Dharma (CrySiS) ransomware strains.
This month, security researcher Jakub Kroustek found a few new Dharma ransomware strains which encrypted the victim’s files with a “.betta” or “.xxxxx” extension. They asked for the ransom to be paid to either the “backtonormal@foxmail.com” or the “syndicateXXX@aol.com” email address.
Even though Jakub Kroustek posted his findings about the @foxmail ransom on October 19, at the time of us writing about the strain we uncovered (November 7), only 44 out of 67 antivirus engines detect the malicious file he uncovered, as you can see on VirusTotal.
Now, in our research, we found another new type of Dharma ransomware, which goes undetected by almost all security solutions.
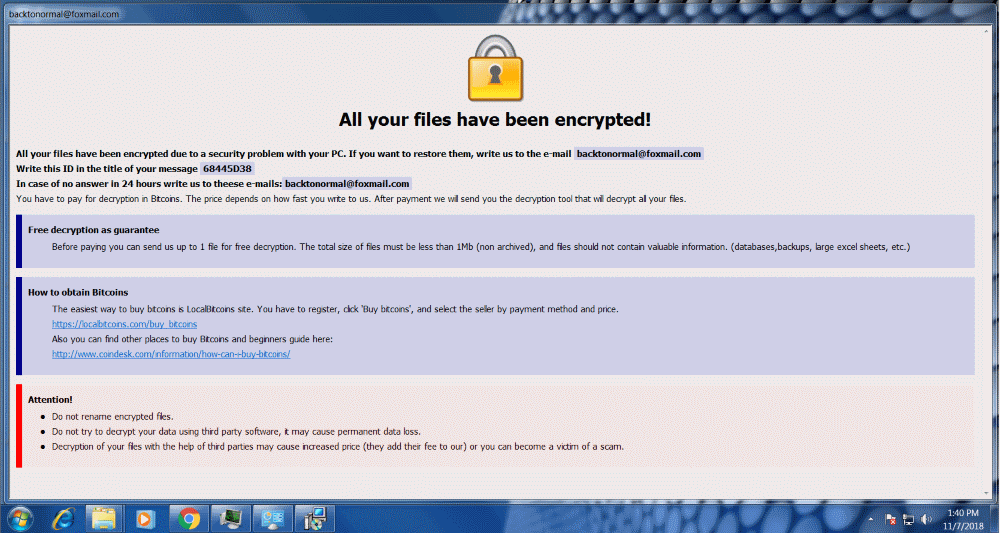
Needless to say, this poses a huge risk to both home users and organizations without proper security layers and awareness.
And yes, it’s the same cybercriminal or group of criminals associated with the backtonormal@foxmail.com email address.
How bad is it?
Only a single antivirus engine picks it up, out of 67 listed.
Even though some details associated with it have been flagged by researchers as malicious for almost 2 years now, because of the nature of the Dharma ransomware, detection levels are critically low.
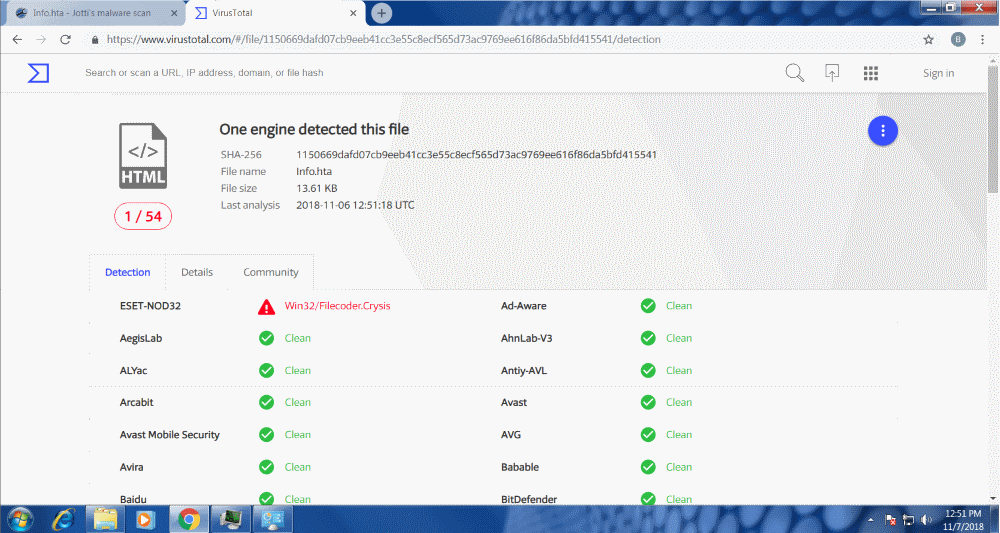
Even when using the Jotti malware scan tool, only 1 out of 15 malware scanners pick up this dangerous ransomware strain.
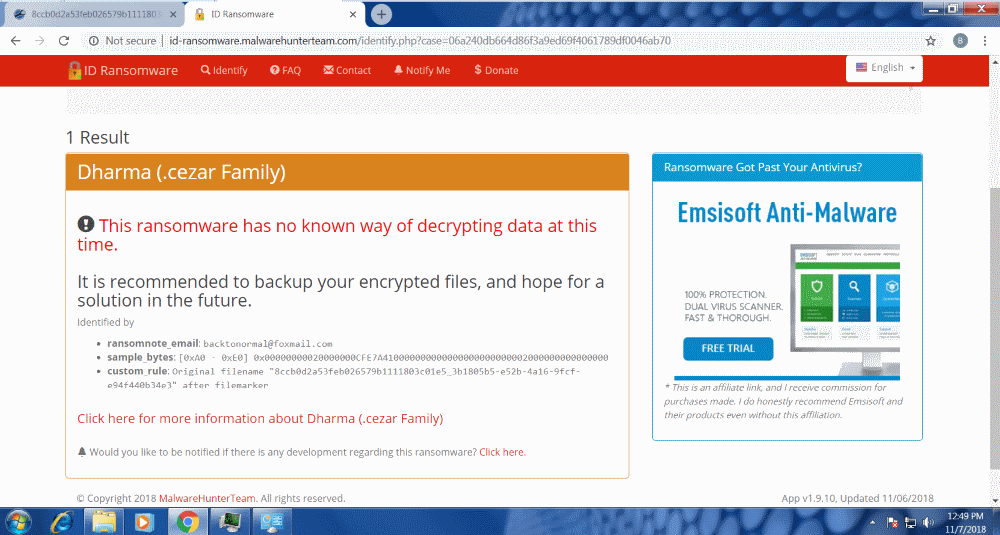
Our own investigation began with a malicious exe dropped through a .NET file and another associated HTA file, which, once unpacked, directs the victim to pay a Bitcoin ransom to the backtonormal@foxmail.com email address.
We double-checked the HTA file using ID-ransomware, a tool that assesses the ransom note, and the result came back as belonging to the Dharma (.cezar ransomware family).
Security researcher Michael Gillespie warned it intensifying back in 2017. Now, he also found a Dharma Ransomware strain that uses a .NET dropper to spread. Once it hits an unprotected device, it will encrypt all files with a “.tron” extension, demanding payment to be made at the xtron@cock.li or xtron@fros.cc email addresses.
He submitted the findings to VirusTotal on November 6, and, at the time of writing this security alert, only 28 out of 66 antivirus engines are capable of detecting this malicious file.
What happened?

As we outlined above, as of now, November 7, only 1 out of 67 Antivirus engines can detect this type of Dharma ransomware. For others’ findings, Antivirus detection is still woefully lagging behind, because of the nature of the infection.
How the infection happens:
From our investigation so far, the infection vector for this particular Dharma ransomware has been the Windows RPD (Remote Desktop Protocol). The malicious executable does not exploit vulnerabilities but uses Trojan-like behavior.
Malicious actors will use tools like remote port scanners to scan enterprise computers, hunting for RDP-enabled endpoints that employees commonly use to log-in from home. Then, once they find an RDP-enabled endpoint, the criminals will try to log by guessing the admin name and brute-force attacking the password. Once that happens, the criminals will copy and execute the ransomware strain. Because they usually have admin rights, the criminals can even turn off those protections put in place, so strong passwords are essential.
Dharma ransomware strains associated with the backtonormal@foxmail.com ransom payment address will encode data formats including but not limited to:
.odc, .odm, .odp, .ods, .odt, .docm, .docx, .doc, .odb, .mp4, .sql, .7z, .m4a, .rar, .wma, .gdb, .tax, .pkpass, .bc6, .bc7, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, .wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps.
Most Dharma ransomware infections happen locally and the strains we uncovered follow the same pattern.
And here comes the worst news: even if you pay the ransom, the attacker will not decrypt your files.
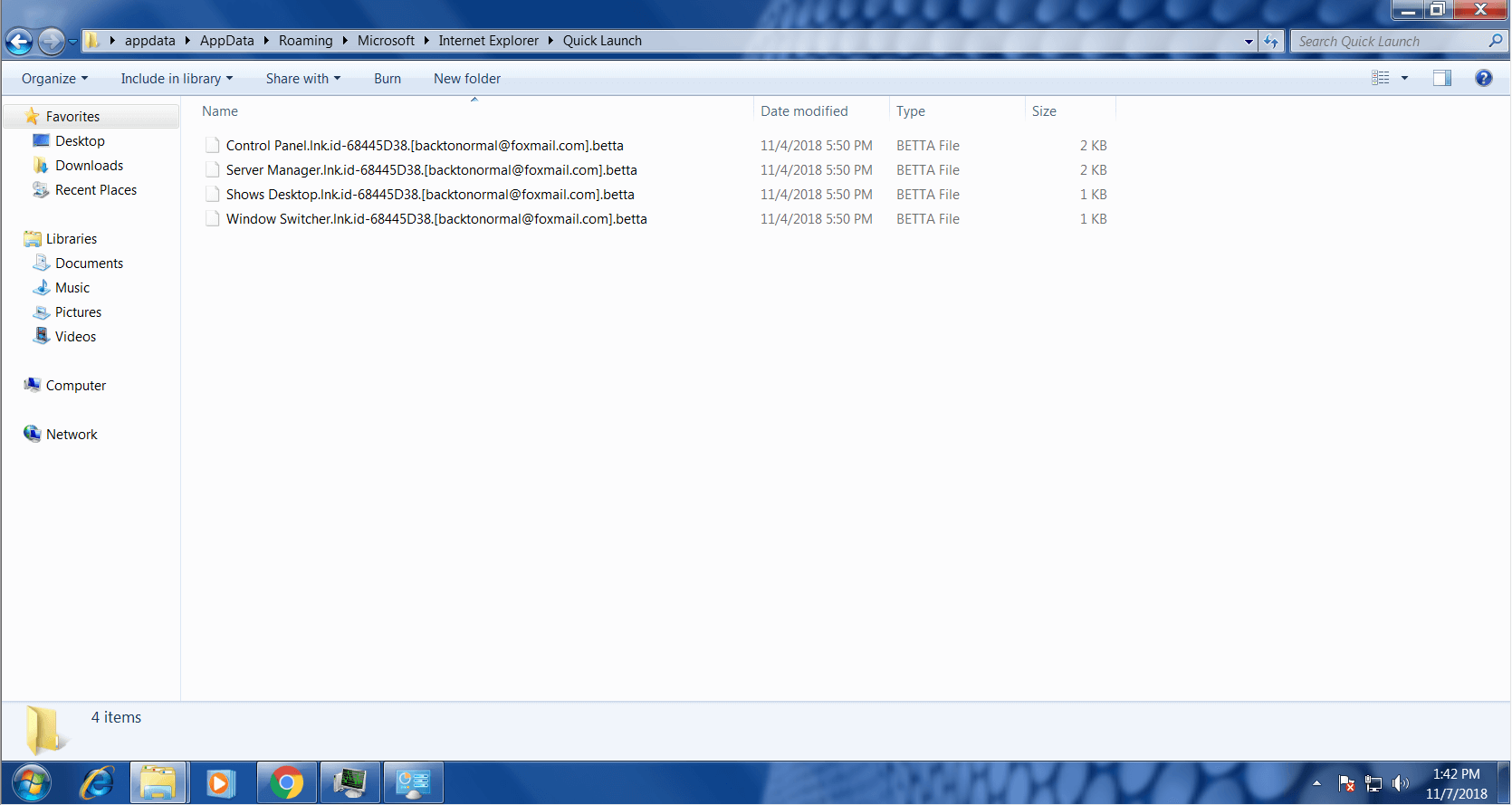
This malware strain and other similar ones will never try to connect to malicious command and control centers. It will generate its encrypting key locally, without sending it back to the attacker, so it’s a fake key.
How to stay safe from the Dharma ransomware:
The only way to be safe from ransomware is to proactively defend your devices by backing up your info often and using multiple security layers, not just Antivirus alone.
For Dharma ransomware in particular, strong passwords and 2-factor authentications are mandatory, for the reasons we outlined above.
The newest Dharma (CrySis) ransomware strains do not have decryption toolsavailable so, in this case, prevention beats the cure. For online safety, we recommend you follow these anti-ransomware security measures:
- Always backup your data in multiple locations. Use external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.) to store it. Our guide will show you how to do it;
- Always keep your software upgraded to their latest versions, as malware and ransomware usually targets outdated programs and apps.
- Keep strong passwords for any account you use, either personal or in a business setting. At an enterprise level, Dharma ransomware can compromise an endpoint through brute-force attacks in order to gain access and execute the malicious file.
- DO NOT open spam emails or download or copy attachments, links or files from unknown sources that could infect your computer;
- For protection from common ransomware strains, consider using multiple security layers. Antivirus should be the base but you should also have proactive, anti-malware security solutions with behavioral analysis. Your browser should have protections like adblockers in place.
- Given the rise of new types of malware, we remind you that security is not just about using all the latest security tools, it’s also about getting educated so you can better spot suspicious activity. These free educational resources can help you gain more knowledge in the cybersecurity field;
- In case you do get infected with ransomware (Dharma or other files), before attempting decryption duplicate your encrypted files and keep a copy safe. That way, if a ransomware decryption tool becomes available in the future, you can eventually restore your files.
- Lastly, never pay the ransom. As you can see, there is no guarantee and almost no chance to recover your data.
- Credit : heimdalsecurity.com



ไม่มีความคิดเห็น:
แสดงความคิดเห็น