Security researchers observed a new ransomware strain dubbed VevoLocker. Its variants have already encrypted multiple websites, including the official webpage of the Ukrainian Ministry of Energy and several Danish webpages.
Before seeing what steps you have to take to avoid this infection, let’s examine it further.
How the infection happens:
Exploiting well-known vulnerabilities in popular CMS systems like Drupal and Remote Desktop Protocol (RDP) accesses, VevoLocker gained access to web servers and encrypted their contents.
The VevoLocker ransomware takes advantage of a few well-known vulnerabilities like Drupalgeddon2.
Once a vulnerable web server is discovered, Vevolocker will encrypt .css., .htm, .html, .js, and .php files, essentially blocking all aspects of a site’s content and functionality.
“Drupalgeddon2 is a highly critical remote code execution bug affecting most Drupal sites which was disclosed at the end of March. It is also possible (although less likely) that someone is already exploiting CVE-2018-7602 which the Drupal team announced just yesterday but has yet to provide a public fix,” explained Craig Young, a Tripwire researcher.
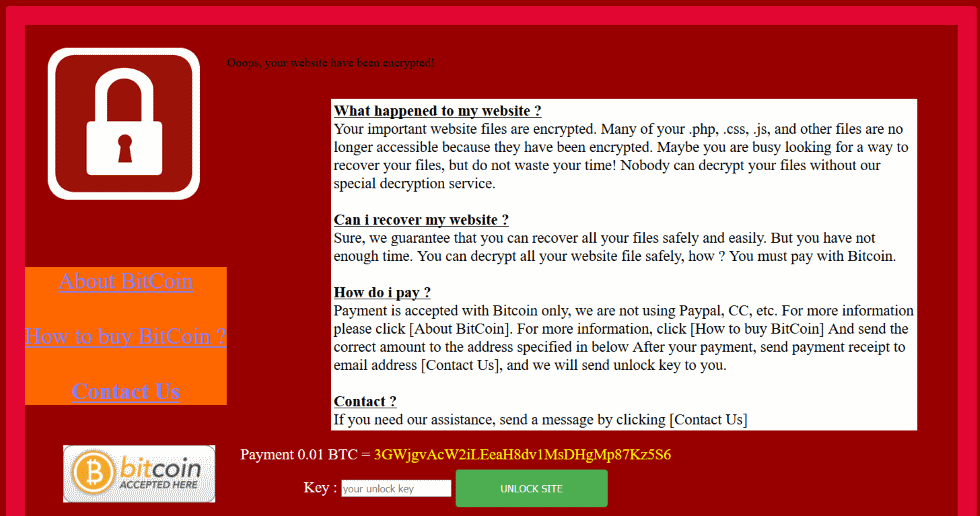
In order to recover their website content, victims have to pay a 0.01 Bitcoin ransom. While that translates to around $90, as with all ransomware attacks, victims have no guarantee of recovering their data.
The VevoLocker ransomware already has a few variants. Victims will see an image like the one above instead of their usual webpage content.
The extorsion messages, received via email or social media, can look like this:
- Locked.
- Ooops!
- Locked by ALx
- Website Locked!
- HACKED BY CENTR1X
- hacked by n00p
- fils are descrypted
Some campaigns have even refered directly to Facebook pages like https://www.facebook.com/bloodsec.gov/ or https://www.facebook.com/andi.s.cliquers2.
How to stay safe from the VevoLocker ransomware:
As VevoLocker does not seem to have a decryption tool available yet, consider the following:
To prevent a ransomware attack, continuously update your CMS software. Then, choose a solution that automatically conducts vulnerability scans of web servers and services.
Another great method to avoid VevoLocker and other ransomware variants is to disable global access to the Remote Desktop Protocol (RDP).
To prevent a ransomware attack, continuously update your CMS software. Then, choose a solution that automatically conducts vulnerability scans of web servers and services.
Another great method to avoid VevoLocker and other ransomware variants is to disable global access to the Remote Desktop Protocol (RDP).
Here is a general anti-ransomware protection plan that will be useful in case of future threat campaigns:
- Always backup your data and use external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.) to store it. Our guide will show you how to do it;
- Always update any CMS or tool you use in order to avoid vulnerabilities.
- Use strong, unique passwords and only share credentials if it’s absolutely mandatory This security guide comes in handy;
- Consider using a paid antivirus software which is also up to date, or consider having a proactive anti ransomware protection (here’s what Heimdal PRO can do for you).
- Prevention is the way to avoid potential financial and data losses. These free educational resources can help you gain more knowledge in the cybersecurity field.
Credit : heimdalsecurity.com



ไม่มีความคิดเห็น:
แสดงความคิดเห็น