Security Alert: GandCrab Ransomware Returns with New Waves of Spam Campaigns
In which the malware is spread via malicious files
You may be familiar with GandCrab ransomware that seems to widely spread via various spam campaigns or social engineering techniques to infect and harvest users’ most important data.This fast-growing malware has infected more than 50,000 victims and targeting mostly the ones from Scandinavia and UK speaking countries, according to a report CheckPoint.
Security researchers recently analyzed a new spam campaign in which malicious actors try to lure victims into clicking a malicious link that will open a binary file and infect users’ system with the GandCrab ransomware.
This phishing campaign has been delivered with the following content (sanitized for your own protection).
Here’s how this email looks like:
From: [Spoof / Forwarded Sender Address]
Subject Line:
Job: Banking Opportunities, Greymouth
Job: Banking Opportunities, Greymouth
Content:
Dear Hiring Manager
Please review my [link: http: // abuellail [.] Com / resume. php] resume
Charlotte Anderson
Email: charlotte.anderson @ abuellail [.] com
Dear Hiring Manager
Please review my [link: http: // abuellail [.] Com / resume. php] resume
Charlotte Anderson
Email: charlotte.anderson @ abuellail [.] com
If a user clicks on the link received on the email, then he will be redirected to one of the following and compromised web pages (sanitized for your online safety):
test.ritsdb [.] com
ubsms [.] com
test.technostark [.] com
ubsms [.] com
test.technostark [.] com
How the infection happens
Basically, the malware is spread via an executable binary file (resume.exe) which is returned after GandCrab is running on the local machine as a file called “bhxsew.exe”.
During the process, the ransomware will try to collect and determine the external IP addresses of the victims via legitimate services such as:
Http: // ipv4bot.whatismyipaddress. com
Http: / /bot.whatismyipaddress. Com
Http: / /bot.whatismyipaddress. Com
The main component of GandCrab is “dropped” as a “bhxsew.exe” file in the <Windows appdata> directory. As part of the local data encryption, this malicious file is configured to communicate with the following domains:
zone alarm [.] bit
ransomware [.] bit
ransomware [.] bit
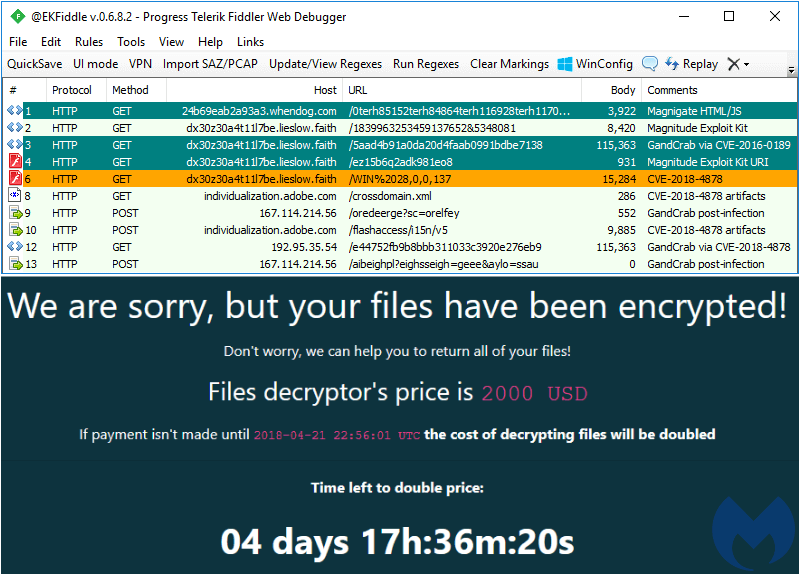
GandCrab ransomware is not spread only via spam emails but also seen distributed via an exploit kit campaign called MagnitudeEK which abuses software vulnerabilities found in Windows, Adobe Flash Player, and Silverlight.
As regards to the MagnitudeEK spam campaign, security researchers have seen a flood of subdomains being used via this site:
lieslow [.] faith
Malwarebytes Labs recently found that Magnitude EK, “which had been loyal to its own Magniber ransomware, was now being leveraged to push out GandCrab, too.”
Here’s how the ransom note is displayed on the infected machine:
Source: Malwarebytes Labs blog
Heimdal Security proactively blocked these infected domains (and malicious emails), so all Heimdal PRO and Heimdal CORP users are protected.
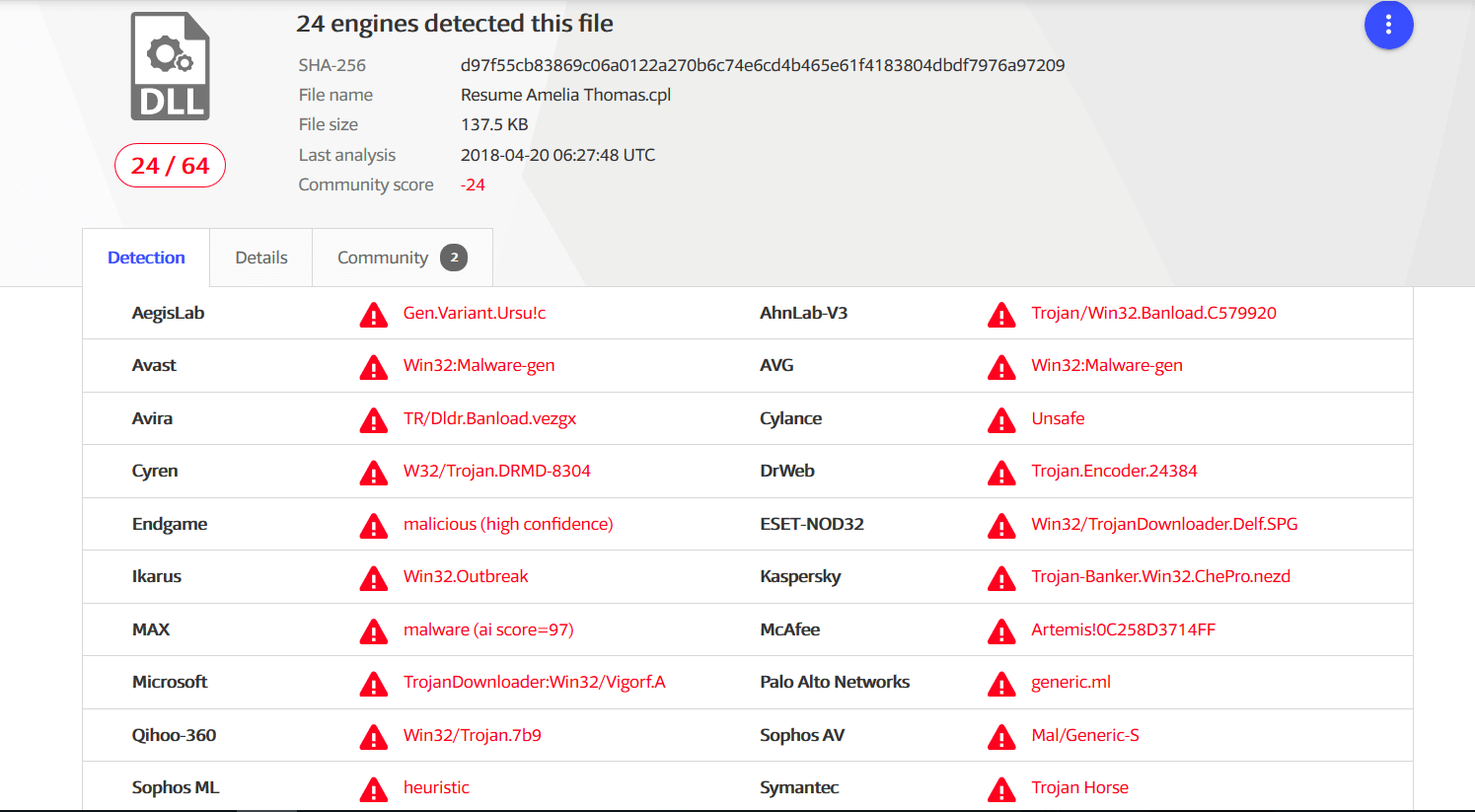
According to VirusTotal, 24 antivirus products out of 64 have detected this spam email campaign at the time we write this security alert.
How to stay safe from the GandCrab ransomware
One of the best ways to keep your important data safe from ransomware is to think and act proactively.
To minimize both the risks and the impact of these online threats, we recommend both home users and companies to use and apply these security measures:
- Always backup your data and use external sources such as a hard drive or in the cloud (Google Drive, Dropbox, etc.) to store it. Our guide will show you how to do it;
- DO NOT open (spam) or download attachments or links from unknown sources that could infect your computer;
- Use strong and unique passwords and never reuse them for multiple accounts. This security guide comes in handy;
- Consider using a paid antivirus software which is also up to date, or consider having a proactive anti ransomware protection (here’s what Heimdal PRO can do for you).
- Prevention is the best cure, so make sure you learn as much as possible about how to easily detect spam emails. These free educational resources can help you gain more knowledge in the cybersecurity field;
- Given the rise of new types of malware (the version 2 of GandCrab ransomware is out there and, unfortunately, there’s no decryption tool available) we remind you that security is not just about using a solution or another, it’s also about improving your online habits and being proactive.
Should you need to understand what ransomware is all about, this dedicated guide will help you.
If you’ve been a victim of the GandCrab ransomware, the good news is that there’s a decryption tool available you can use to recover the valuable data locked by ransomware.
Credit : heimdalsecurity.com



ไม่มีความคิดเห็น:
แสดงความคิดเห็น